#scrap data from H&M
Explore tagged Tumblr posts
Text
PROMPT #26: Last
The following is the contents of the last pages written in the journal of Ludo Swiftwind, recovered from Carteneau Flats in the wake of Omega's activation.
DON'T FORGET:
YOU ARE HERE TO RECOVER THE PRIMAL KILLER.
Adeledji's crew estimate its worth at several billion gil; Lolorito will likely pay more (enough to settle debts and then disappear for good)
Keep notes about anything important because something down here is interfering with your short-term memory. For the love of Halone DON'T read anything aloud!
Ashelia M. Riot is your partner and the leader of the Riskbreakers. She is an Ala Mhigan Highlander and she has pink hair, dark brown skin and eyes like desert amethysts (if amethysts could glare at you). You love her very much.
(ask her what the M stands for when you're back)
Don't read anything aloud and don't talk about anything you don't want to have used against you. This sorry piece of scrap sure has a hell of an attitude for something that crash-landed here a few thousand years ago.
COME BACK WITH SOMETHING TO SHOW FOR YOUR EFFORTS OR DON'T COME BACK AT ALL. The Syndicate sniff out blood like a Garlean recruiter; they'll expect you to come back empty-handed.
Still about 250M gil deep in the red but interest is going to be the real ###### to get in front of so do something soon
Determined that this is not a primal killer, more like a primal prison. Asked if it had any primals left and of course it's clammed up.
NEW MISSION (?): Convince it to part with a primal
You are Ludo Swiftwind and you hail from Riversmeet. You became a trader to see the world and you survived the Calamity (most of you did, anyway) and the thing you want most (to go back) isn't going to happen
If you ever forget what Coerthas looked like in the summer you may as well just give up
(just remembered the M stands for Marco.)
You fell in love with Ashe the first time you saw her lost in her own thoughts. Can't remember where you were but she was definitely back in Ala Mhigo and you knew you wanted to take her there for true.
might not make it out might not ᴍꬰʞƐ it out might not
Found records detailing the subjugation of Sephirot, Sophia, and Zurvan (sp?)
See back cover for translations of Allagan phrases
(Maybe if I upload this data onto a tomestone it'll be enough to cover at least the first billion.)
if $exit=1 apologize to Ashe endif
I want to see her again but I fucked somethinꬶ up
You are Ōsamu bas Maevius and you are a stupid little h###-##### who couldn't even hack it in the provinces because it took you six years after you ran away to consider that your mother might have had trauma
she even told you once that she wanted to go home but they wouldn't let her back in, how much clearer could she have been
had the info on the Allag primals directly into my memory, ineꜰꜰicient but got the job done (finally just told it i had enemies i needed to beat and something clicked)
ꞵeautiful battles th0usands of years ago, check combat data logs for ver1f1cation, life and death in ꞵalance, will s4tisfy SYNDICATE LEECHES for maybe 1 year so should run fast
DATA TRANSMISSION BLOCKED SEE FRONT COVER FOR PRIMAL COORDINATES if you can't find them keep going higher
tried to stay in riversmeet but the cold felt too much like home
01100111 01101111 01101111 01100100 01100010 01111001 01100101 00100000 01110111 01101111 01110010 01101100 01100100
Ꞷ
5 notes
·
View notes
Text
Black Friday, textile waste and considerations for a sustainable future

It is appropriate to address related aspects that, almost certainly, will be generated after the Black Friday purchases, encouraged on days like this.
The effects of fast-fashion are noticeable every day of the year, with textile waste being a problem similar to that generated by plastic[1], since the truth is that more than 92 million tons of clothing are sent to landfills each year and there is no separate collection of this waste stream for the time being. Other alarming data are that in Spain annual consumption per person is between 7 and 10 kg of clothing, most of which can be classified as disposable, which generates textile waste in an almost uncontrolled manner. According to data available from public administrations, textile waste represents 5% of municipal waste generated.
The new legislation on the circular economy and waste management[2] establishes a series of obligations, such as all those related to the expanded responsibility of the producer: new product design obligations to encourage recycling; duty to accept the return of reusable products[3]; duty to assume the financial obligations corresponding to the costs of separate collection, transportation, waste treatment and even cleaning public roads, if applicable. Thus, for example, under the name of the Asociación para la Gestión del Residuo Textil (AGRT) (Association for the Management of Textile Waste)[4], the constitution of a collective system of extended producer responsibility (SCRAP)[5] is planned, of which the multinationals Decathlon, H&M, Ikea, Inditex, Kiabi, Mango will be part and Tendam, and with which they plan to collectively comply with these new obligations enforceable as of December 31, 2024.[6]
Regional administrations and local entities must promote and implement separate collection for the subsequent treatment of textile waste. This obligation falls on local entities that, in the exercise of their powers, must implement a collection model that enables them to meet the objectives of separate collection, reuse and recycling set for textile waste in community and state regulations.
We understand it is necessary to have the voluntary collaboration of private collection points. That is, in order to encourage the delivery of textile waste by individuals for proper management, producers and distributors of textile products must be able to implement collection systems in a way that favours reverse logistics[7] and the return of textile products once used, and without being considered a waste manager, as long as they limit themselves to receiving textile waste delivered by individuals and do not carry out any type of waste management activity.
It is necessary to mention the new obligations that will come from the European Union regarding due diligence in matters of sustainability that will affect companies in the sector with more than 250 workers or with a global business volume of more than 40 million euros. This standard will force you to integrate due diligence into your business strategies[8]. This will entail establishing the actual or potential negative effects on the environment of its activity and the value chain, preventing, stopping or mitigating said adverse effects, the effectiveness of the strategy and due diligence measures and, ultimately, establishing a claim procedure.
There will also be standards on product sustainability (Ecodesign for Sustainable Products Regulation - ESPR)[9], on labelling, a digital product passport for textiles, or on the substantiation of the environmental information that companies use to promote the products they introduce into the market. In this regard, the new Green Claims Directive[10], which is about to be approved, aims to establish common criteria against greenwashing[11], in order to apply greater control and transparency to environmental information and the so-called environmental labelling that companies use, voluntarily, to promote their products. Indeed, the future standard establishes minimum standards on how to substantiate and communicate this type of declaration (which must be specific to all or part of the product, truthful, precise, verifiable and justified).
All these considerations taken together and without a doubt, can serve to anchor the aforementioned fast-fashion, although they may not be enough if we do not have binding ecodesign standards, for example. Now, we are already facing a paradigm shift that, over time, will provide us with means to better prevent littering and, where appropriate, mitigate the negative environmental impacts of textile products, as well as promote reuse and high quality recycling. At least we have hope.
Source
Víctor Moralo Iza, Black Friday, residuos textiles y consideraciones para un futuro sostenible, in: El País, 24-11-2023, https://cincodias.elpais.com/cincodias/2023/11/24/legal/1700810526_982955.html
[1] Read also: https://www.tumblr.com/earaercircular/728619189968027648/will-we-ever-be-able-to-recycle-our-clothes-like?source=share
[2] Read also: https://earaercircular.tumblr.com/post/684755137609252864/what-the-spanish-waste-law-brings-harmonization
[3] https://www.europarl.europa.eu/RegData/etudes/BRIE/2023/745707/EPRS_BRI(2023)745707_EN.pdf
[4] These days the news is the “birth” of the first collective system for the management of textile waste in Spain: Seven multinationals from the textile industry have joined together in what is the first Collective System of Extended Producer Responsibility (SCRAP) in the sector, with the aim of giving "a collective boost" to textile recycling in Spain. The so-called Association for the Management of Textile Waste (AGRT) is supported by the companies Decathlon, H&M, Ikea, Inditex, Kiabi, Mango and Tendam. https://www.productordesostenibilidad.es/2023/01/una-asociacion-para-la-gestion-del-residuo-textil-agrt/
[5] Sistema Colectivo de Responsabilidad Ampliada del Productor (SCRAP). Read also: https://www.tumblr.com/earaercircular/721717700267753472/as-of-last-saturday-on-textile-producers-in-the?source=share
[6] Read also: https://www.tumblr.com/earaercircular/734956569878560768/waste-without-management-systems-for-waste-and?source=share
[7] Read also: https://www.tumblr.com/earaercircular/665487447558438912/dutch-start-up-raises-millions-in-investment-to?source=share
[8] In line with green transition in the EU, fresh policy proposals are making their way forward. One of them, the CSDDD/CS3D – if adopted – requires serious steps to be taken by companies. Obligations regarding corporate sustainability due diligence along the full value chain are to be expected. The directive aims to make large companies responsible for environmental and human rights violations that occur along their value chains. Thus, companies are mandated to identify and address impacts on human rights and the environment, integrating due diligence into their operational strategies. Company directors are tasked with overseeing due diligence implementation and incentivized to contribute to climate change mitigation. https://www.dentons.com/en/insights/articles/2023/november/9/new-legislative-proposal-on-corporate-sustainability-due-diligence-directive
[9] The proposal for a new Ecodesign for Sustainable Products Regulation (ESPR), published on 30 March 2022, is the cornerstone of the Commission’s approach to more environmentally sustainable and circular products. The proposal builds on the existing Ecodesign Directive, which currently only covers energy-related products. https://commission.europa.eu/energy-climate-change-environment/standards-tools-and-labels/products-labelling-rules-and-requirements/sustainable-products/ecodesign-sustainable-products-regulation_en
[10] What is the Green Claims Directive? The Green Claims Directive aims to stop greenwashing by setting standards for environmental claims. The spark came from a 2020 study showing that 53% of environmental claims in the EU were vague or misleading. https://environment.ec.europa.eu/publications/proposal-directive-green-claims_en
[11] Read also: https://www.tumblr.com/earaercircular/729425164711886848/sustainability-more-information-is-forthcoming?source=share
0 notes
Text
How to Extract Product Data from H&M with Google Chrome?
Data You Can Scrape from H&M
Product’s Name
Pricing
Total Reviews
Product’s Description
Product’s Details

Requests
Google’s Chrome Browser: You would require to download the Chrome browser and the extension requires the Chrome 49+ version.
Web Scraping for Chrome Extension: Web Scraper extension could be downloaded from Chrome’s Web Store. Once downloaded the extension, you would get a spider icon included in the browser’s toolbar.
Finding the URLs
H&M helps you to search products that you could screen depending on the parameters including product types, sizes, colors, etc. The web scraper assists you to scrape data from H&M as per the requirements. You could choose the filters for data you require and copy corresponding URLs. In Web Scraper toolbars, click on the Sitemap option, choose the option named “Edit metadata’ to paste the new URLs (as per the filter) as Start URL.
For comprehensive steps about how to extract H&M data, you may watch the video given here or continue to read:
Importing H&M Scraper
After you install the extension, you can right-click anyplace on the page and go to the ‘Inspect’ option as well as Developer Tool console would pop up. Just click on the ‘Web Scraper’ tab and go to the ‘Create new sitemap’ option as well as click on the ‘Import sitemap’ button. Now paste JSON underneath into Sitemap’s JSON box.
Running the Scraper
To start extracting, just go to the Sitemap option and click the 'Scrape' alternative from the drop-down menu. Another window of Chrome will come, permitting the extension for scrolling and collecting data. Whenever the extraction is completed, the browser will be closed automatically and sends the notice.
Downloading the Data
For downloading the extracted data in a CSV file format, which you could open with Google Sheets or MS Excel, go to the Sitemap’s drop-down menu > Export as CSV > Download Now.
Disclaimer: All the codes given in our tutorials are for illustration as well as learning objectives only. So, we are not liable for how they are used as well as assume no liabilities for any harmful usage of source codes. The presence of these codes on our website does not indicate that we inspire scraping or scraping the websites given in the codes as well as supplement the tutorial. These tutorials only assist in illustrating the method of programming data scrapers for well-known internet sites. We are not indebted to offer any help for the codes, in case, you add your different questions in a comments sector, and we might occasionally address them.
#scrap data from H&M#importing H&M scraper#product data scraping#Web scraper#Data scraping services#Extract product data
1 note
·
View note
Text
Pyroraptor olympius

By Ripley Cook
Etymology: Fire Thief
First Described By: Allain & Taquet, 2000
Classification: Dinosauromorpha, Dinosauriformes, Dracohors, Dinosauria, Saurischia, Eusaurischia, Theropoda, Neotheropoda, Averostra, Tetanurae, Orionides, Avetheropoda, Coelurosauria, Tyrannoraptora, Maniraptoromorpha, Maniraptoriformes, Maniraptora, Pennaraptora, Paraves, Eumaniraptora, Dromaeosauridae
Status: Extinct
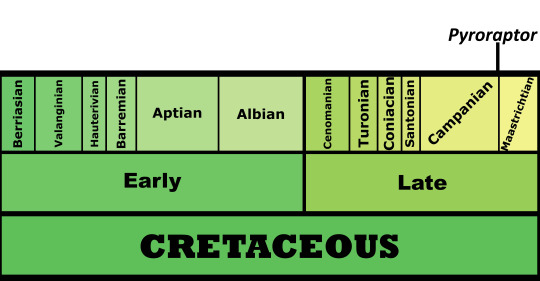
Time and Place: Around 72 million years ago, in the Campanian of the Late Cretaceous
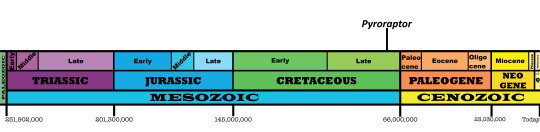
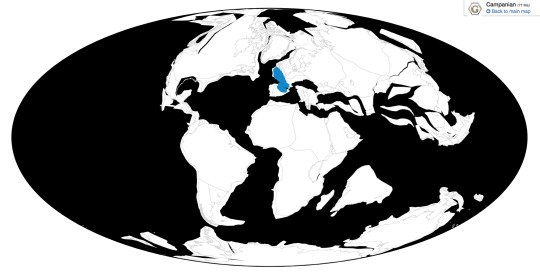
Pyroraptor is known from the La Boucharde locality in France, the Vitoria and La Posa Formations in Spain, and potential locations in the UK
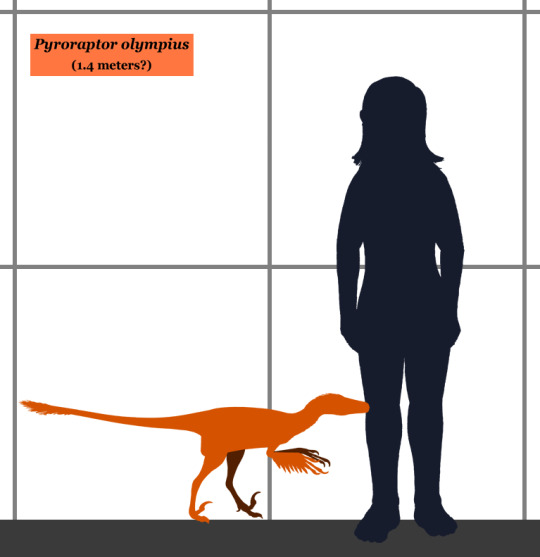
Physical Description: Pyroraptor is a poorly known raptor, based on a few fossil scraps found around the late Cretaceous of Europe. Portions of the foot, arms, and some teeth are known from Pyroraptor, none preserved very well. It had the sickle second toe claw of other raptors, and it seems to have been fairly lightweight and small - probably no longer than 1.4 meters, though that is of course an estimate. Other than that, we know very little about its appearance - we don’t even know if it was a specialized sort of raptor like in the Dromaeosaurine, Microraptorine, or other groups - except for that it would have been very fluffy, with wings on its arms and a tail fan on its tail.
By Conty, CC BY 3.0
Diet: As a raptor, it is most likely that Pyroraptor fed upon meat, probably small animals such as lizards, mammals, and turtles.
Behavior: Pyroraptor would have been a very active dinosaur, spending most of its time hopping and stalking around the rivers and beaches in its island environment. Like other raptors, it wouldn’t have been a pursuit predator, but rather an ambush one: it would have waited for prey to appear, and then pounced on it, using rapid flaps of its wings to stay balanced on top of the struggling prey. This technique, called raptor prey restraint, is still seen in living raptors today. Pyroraptor would have also been able to run up vertical surfaces, such as trees and cliffs, using flaps of its wings to gain lyft up the surface. Then, it would have been able to catch food on the run! Other than that, Pyroraptor probably wasn’t very social, based on fossil evidence from other raptors - that being said, it would have taken care of its young, and probably stayed in small family groups during this process.

By The Unknown Horror From the Ocean Depths, CC BY-SA 4.0
Ecosystem: Pyroraptor lived in the Late Cretaceous of Western Europe, which was a series of islands sitting in a shallow ocean - sort of like the Bahamas today. These ecosystems were easy to travel between, utilizing rafting and other forms of impromptu sea travel, so the animals on them tended to be similar to each other. Pyroraptor itself lived with many turtles, snakes, sharks, and gars; as well as Eusuchians such as Musturzabalsuchus and Acynodon. There was some sort of large Azhdarchid pterosaur, too - currently called Azhdarcho, though that’s a questionable assignment. As for other dinosaurs, there were Abelisaurids there, Titanosaurs like Lirainosaurus, Nodosaurids like Struthiosaurus, the Ornithopod Rhabdodon, and another raptor called Richardoestesia, and the protobird Gargantuavis!

By José Carlos Cortés
Other: Pyroraptor was named as such because it was discovered after the occurence of a forest fire. Since so little is known about this dinosaur, there isn’t much more to be said about its phylogenetics or history of discovery! It is rather famous for having been featured in the 2003 documentary Dinosaur Planet, though given its poorly preserved nature, the wisdom in that choice of star is mildly suspect.
~ By Meig Dickson
Sources Under the Cut
Allain, R. and P. Taquet. 2000. A new genus of Dromaeosauridae (Dinosauria, Theropoda) from the Upper Cretaceous of France. Journal of Vertebrate Paleontology 20(2):404-407
Allain, R., and X. Pereda Suberbiola. 2003. Dinosaurs of France. Comptes Rendus Palevol 2:27-44
Angst, D., E. Buffetaut, J. C. Corral and X. Pereda-Suberbiola. 2017. First record of the Late Cretaceous giant bird Gargantuavis philoinos from the Iberian Peninsula. Annales de Paléontologie
Astibia, H., E. Buffetaut, A. D. Buscalioni, H. Cappetta, C. Corral, R. Estes, F. Garcia-Garmilla, J. J. Jaeger, E. Jiminez-Fuentes, J. Le Loeuff, J. M. Mazin, X. Orue-Etexebarria, J. Pereda-Suberbiola, J. E. Powell, J. C. Rage, J. Rodriguez-Lazaro, J. L. Sanz and H. Tong. 1990. The fossil vertebrates from the Lano (Basque Country, Spain); new evidence on the composition and affinities of the Late Cretaceous continental faunas of Europe. Terra Nova 2:460-466
Carpenter, K. (1998). "Evidence of predatory behavior by theropod dinosaurs". Gaia. 15: 135–144.
Carpenter, K. 2002. Forelimb biomechanics of nonavian theropod dinosaurs in predation. Senckenbergiana Lethaea 82: 59 - 76.
Carrano, M. T., and S. D. Sampson. 2008. The phylogeny of Ceratosauria (Dinosauria: Theropoda). Journal of Systematic Palaeontology 6(2):183-236
Chanthasit, P., and E. Buffetaut. 2009. New data on the Dromaeosauridae (Dinosauria: Theropoda) from the Late Cretaceous of southern France. Bulletin de la Société Géologique de France 180(2):145-154
Delcourt, R., and O. N. Grillo. 2014. On maniraptoran material (Dinosauria: Theropoda) from Vale do Rio do Peixe Formation, Bauru Group, Brazil. Revista Brasileira de Paleontologia 17(3):307-316
Erickson, G. M., K. Curry Rogers, D. J. Varricchio, M. A. Norell, X. Xu. 2007. Growth patterns in brooding dinosaurs reveals the timing of sexual maturity in non-avian dinosaurs and genesis of the avian condition. Biology Letters 3 (5): 558 - 61.
Fowler, D. W., E. A. Freedman, J. B. Scannella, R. E. Kambic. 2011. The Predatory Ecology of Deinonychus and the Origin of Flapping in Birds. PLoS ONE 6 (12): e28964.
Gauthier, J., K. Padian. 1985. Phylogenetic, Functional, and Aerodynamic Analyses of the Origin of Birds and their Flight. Hecht, M. K., J. H. Ostrom, G. Viohl, P. Wellnhofer (ed.). The Beginnings of Birds. Proceedings of the International Archaeopteryx Conference, Eichstätt: Freunde des Jura-Museums Eichstätt: 185 - 197.
Gishlick, A. D. 2001. The function of the manus and forelimb of Deinonychus antirrhopus and its importance for the origin of avian flight. In Gauthier, J., L. F. Gall. New Perspectives on the Origin and Early Evolution of Birds. New Haven: Yale Peabody Museum: 301 - 318.
Godefroit, P., P. J. Currie, H. Li, C. Y. Shang, and Z.-M. Dong. 2008. A new species of Velociraptor (Dinosauria: Dromaeosauridae) from the Upper Cretaceous of northern China. Journal of Vertebrate Paleontology 28(2):432-438
López-Martínez, N. 2000. Eggshell sites from the Cretaceous-Tertiary transition in south-central Pyrenees (Spain). In A. M. Bravo & T. Reyes (ed.), First International Symposium on Dinosaur Eggs and Babies, Extended Abstracts 95-115
Manning, Phil L., Payne, David., Pennicott, John., Barrett, Paul M., Ennos, Roland A. (2005) "Dinosaur killer claws or climbing crampons?" Biology Letters (2006) 2; pg. 110-112.
Martyniuk, M. 2016. You’re Doing It Wrong: Microraptor Tails and Mini-Wings. DinoGoss Blog.
Pereda-Suberbiola, X., H. Asibia, X. Murelaga, J. J. Elzorza, and J. J. Gomez-Alday. 2000. Taphonomy of the Late Cretaceous dinosaur-bearing beds of the Lano Quarry (Iberian Peninsula). Palaeogeography, Palaeoclimatology, Palaeoecology 157:247-275
Prum, R.; Brush, A.H. (2002). “The evolutionary origin and diversification of feathers”. The Quarterly Review of Biology. 77 (3): 261–295.
Rothschild, B., Tanke, D. H., and Ford, T. L., 2001, Theropod stress fractures and tendon avulsions as a clue to activity: In: Mesozoic Vertebrate Life, edited by Tanke, D. H., and Carpenter, K., Indiana University Press, p. 331-336.
Senter, P., R. Barsbold, B. B. Britt and D. A. Burnham. 2004. Systematics and evolution of Dromaeosauridae (Dinosauria, Theropoda). Bulletin of the Gunma Museum of Natural History 8:1-20
Torices Hernández, A. 2002. Los dinosaurios terópodos del Cretácico Superior de la Cuenca de Tremp (Pirineos Sur-Centrales, Lleida). Coloquios de Paleontología 53:139-146
Torices, A., P. J. Currie, J. I. Canudo and X. Pereda-Suberbiola. 2015. Theropod dinosaurs from the Upper Cretaceous of the South Pyrenees Basin of Spain. Acta Palaeontologica Polonica 60(3):611-626
Turner, Alan H.; Pol, D.; Clarke, J.A.; Erickson, G.M.; Norell, M. (2007). “A basal dromaeosaurid and size evolution preceding avian flight”. Science. 317 (5843): 1378–1381.
Turner, AH; Makovicky, PJ; Norell, MA (2007). “Feather quill knobs in the dinosaur Velociraptor”. Science. 317 (5845): 1721.
Vila, B., M. Suñer, A. Santos-Cubedo, J. I. Canudo, B. Poza and A. Galobart. 2011. Saurischians through time. In A. Galobart, M. Suñer, & B. Poza (eds.), Dinosaurs of Eastern Iberia 130-168
Weishampel, David B.; Dodson, Peter; and Osmólska, Halszka (eds.): The Dinosauria, 2nd, Berkeley: University of California Press. 861 pp.
Xu, X.; Zhou, Z.; Wang, X.; Kuang, X.; Zhang, F.; Du, X. (2003). “Four-winged dinosaurs from China”. Nature. 421 (6921): 335–340.
#Pyroraptor olympius#Pyroraptor#Raptor#Dinosaur#Bird#Birblr#Palaeoblr#Dromaeosaur#Dinosaurs#Factfile#Birds#Cretaceous#Eurasia#Carnivore#Theropod Thursday#paleontology#prehistory#prehistoric life#biology#a dinosaur a day#a-dinosaur-a-day#dinosaur of the day#dinosaur-of-the-day#science#nature#Feathered Dinosaurs
386 notes
·
View notes
Photo






Computing Career
Created for: The Sims 4 by Hayran
Tech Guru's career is good explored and well worked on The Sims 4 about some IT/Computing stuffs, but I'd like something more "get the hands dirty", close to the reality I live when it comes to working with computers (I work with IT/computing IRL, more with hardware). The objective is to make something more "industrial/company working in", but without losing the way of "The Sims like", with little humor, and freedom in promotions and job roles. So, in this career you can will work more with skills like handiness, logic and programming, having available two track; Computer Engineer in the focus on handiness and logic, and Computer Scientist on the focus in logic and programming, with 10 levels and fair day off system (most closer of careers of TS4). This career does not replace Tech Guru, so you can have both without any problems.
Download: http://modthesims.info/d/622547/computing-career.html
Get featured: https://maxismatchccworld.tumblr.com/
Career details:
Computing Quote:Does the world of computers fascinate you? So get into the computer career and become a Computer Nerd. Take the control of computers before they control you! Or at the very least try it... Location: Simlicon Valley Industries Level 1 - Scrap Organizer Quote:There's nothing better than starting the job in computing having contact with the soul of computers, you as a Scrap Organizer need to get the hands dirty and separate the old computer boards properly for recycling, after all, computers boards in addition to silicon, have gold and silver in, then we're not going to want to waste it, right? §28 H / §196 D Work Schedule: M-T-W-T-F / 7 hours shift Mood: Focused Objective(s): Logic 2 Level 2 - Silicon Mixer Quote:The hard work still goes on, and as a Silicon Mixer, you have the job of mixing all the basic elements that will be used in the process of manufacturing computer boards. In addition to the heavy duty, you've gained a new scent that comes from the mixers, at least your new odor will ward off the annoying technophobic Sims. §36 H / §252 D Work Schedule: M-T-W-T-F / 7 hours shift Mood: Focused Objective(s): Programming 2 Level 3 - Beta Tester Quote:You've studied the basics of programming and so your supervisors have temporarily moved you to the software development department in the industry as a Beta Tester for test your basics programming skills. You need to test and report all problems such as bugs, encountered during software testing. In the end, just remember! That the bug fix process is not spray insecticide on the computer! §45 H / §315 D Work Schedule: M-T-W-T-F / 7 hours shift Mood: Focused Objective(s): Handiness 2 Level 4 - Soldering Whiz Quote:Your supervisors gave you a promotion where you get back to dirty your hands, now you need to learn how to deal with welding and become a Soldering Whiz. This process is very important to learn how to repair parts and test your knowledge on handiness in hardware. Follow the printed traces on the circuit boards and steer the trace to success! §60 H / §420 D Work Schedule: M-T-W-T-F / 7 hours shift Mood: Focused Objective(s): Logic 3 - Handiness 4 Level 5 - Support Technician Quote:You've reached a career position that needs to handle a lot of workload. As Technical Support you need to work on implementing new technologies, or deal with hardware or software maintenance, but mostly solving file a request from users with computer-related problems, in a nutshell help-desk services. But do not worry, sometimes when you will go to fix the problem, the user's computer will self-repair. At least temporarily, until he calls you again. §65 H / §455 D Work Schedule: M-T-W-T-F / 7 hours shift Mood: Focused Objective(s): Programming 3 - Logic 4 Level 6 - Systems Analyst Quote:It's time to take a sit a bit and use your logical and programming skills to work. You are now a Systems Analyst. Develop small programs, estimates new computer products needs, implement IT solutions and lead the small IT team. Try to drink a lot of coffee to stay awake and sometimes tea to calm down... For you will spend most of the time trying to explain in company meetings that the IT department does not handle installation or problems related to air-conditioners(A/C). §75 H / §525 D Work Schedule: M-T-W-T-F / 7 hours shift Mood: Focused Objective(s): Logic 5 - Programming 4 Computer Engineer Track Quote:You've gone through all the steps within your computing career and you saw that passion is precisely the part of creation, to deal more with the hardware manufacturing and design it, so is the Computer Engineer. Develop, create and bring to the world your trend in computers. Level 7 - Circuit Designer Quote:Before designing, you need to plan and as a Circuit Designer you have this job. Focus on designing circuits using your logic skills to design the basics, and simulate your designs before deploying, after all any flaw can mean loophole for rebellion of computers machines against the Sims in the world. §121 H / §847 D Work Schedule: M-T-W-T-F / 7 hours shift Mood: Focused Objective(s): Logic 6 - Handiness 5 Level 8 - Microcontroller Specialist Quote:You have become a Microcontroller Specialist and now you need to integrate all the internal circuits correctly, try to unite and reduce as much as possible, then implement this technology into anything you see, it could be a pencil on your desk, a cup of coffee, even a simple paper clip, so you'll use the computers to fulfill Sims desires without them noticing ... And who knows, too, manipulates them? §169 H / §1183 D Work Schedule: T-W-T-F / 7 hours shift Mood: Focused Objective(s): Logic 7 - Handiness 8 Level 9 - Thinking Machine Architect Quote:It's time to design computer machines that go beyond the simple 'Hello World', you are now the Thinking Machine Architect, develop robots and smart computers to satisfy the wishs of Sims. Just try not to leave loopholes for the rebellion of the computers machines and also, most importantly, try not to develop a smart computer machine capable of creating other smart computers machines, else you will lose your job. Really! §200 H / §1200 D Work Schedule: T-W-T-F / 6 hours shift Mood: Focused Objective(s): Logic 8 - Handiness 10 Level 10 - Computer Engineer Visionary Quote:Congratulations. Now who uses a computer device, is using a part of what you have created. Most of the design and assembly on computers have to have their signature and guarantee. You can be proud that, at least, the computers will have some of your beauty in from now on, and this is notable by other sims that use computer devices. §400 H / §2000 D Work Schedule: T-W-S / 5 hours shift Mood: Focused Computer Scientist Track Quote:You went through every step of your career and noticed that always liked how the computer can be controlled with implementation of new theories, using math logic and programming. So is the Computer Scientist, formulate, theorize, create software and new languages used by them. Be one of the brains behind computing. Level 7 - Statistical Programmer Quote:Now your job is to collect and manage data in computing and how they can be used in software projects to improve the day-to-day of life of Sims. Develop and learn more about the deep desires of Sims, which in the end, you can even manipulate them to your will, through computer systems. §131 H / §917 D Work Schedule: M-T-W-T-F / 7 hours shift Mood: Focused Objective(s): Logic 6 - Programming 5 Level 8 - Kernel Developer Quote:It's time to program and define how the computer brain will work, and make you part of the brain behind the computers. Program computers using your logical and programming skills and set operating laws for computer devices, to ensure, that at least, YOU are not caught up in any possible machine computer rebellion. §180 H / §1260 D Work Schedule: T-W-T-F / 7 hours shift Mood: Focused Objective(s): Logic 8 - Programming 6 Level 9 - Digital Theorist Quote:How will technology be in the future? What can be programmed to improve the life of Sims? How to use digital space to solve problems that do not even exist? What will be of Sims without computer and computers without of Sims? Do we dominate the computers or do they dominate we? For this and other questions, you are responsible now for answering, elaborate logic mathematical to transform and the converter it in programming, to try, to predict a bit of the future, or to dictate as will be in part that. §222 H / §1332 D Work Schedule: T-W-T-F / 6 hours shift Mood: Focused Objective(s): Logic 10 - Programming 8 Level 10 - Computer Scientist Genius Quote:Congratulations. Now you known as Computer Genius, you are almost always asked to predict new technologies, approve magnificent projects, elaborate technological theories, approve new programming languages and set the course for computers machines, as well as do many lectures, and in the end, you can rest assured that you have completely mastered and control the way of thinking of the computers machines... Or not! §500 H / §2500 D Work Schedule: T-T-S / 5 hours shift Mood: Focused
13 notes
·
View notes
Text
Doctor
Clawed footsteps echoed down the metal structure of the half-finished CORE. The machine wasn’t operational, and workers moving among its components typically wore safety harnesses hooked to rails. The masked welder frowned when he realized he couldn’t hear the telltale sliding of a hook along the nearby rail accompanying those footsteps. “D-Doctor!” The young lizard yelled as she approached, loud enough to be heard over the sound of machinery and construction. “It’s t-t-time!” The welder leaned back, switching his torch off and lifting his mask. Three extra white-gloved hands flickered into view, lifting the torch away, and another pair started to unhook his mask. He didn’t need to look up to know who it was, nor that she’d once again gotten overexcited and forgotten to affix her safety gear. “Alphys, harness.” “Wh- oh! S-s-sorry, Doctor!” Alphys replied, fumbling with her hook and finally getting it onto the rail. “Y-you’re, just--”
She faltered as he stood. The welder was an imposing seven feet three inches tall, broad-shouldered and thin, and despite his relative youth he had the experience to back up the authority he’d been given. Still, when he turned, he had that same childish kindness in his smile that she’d come to know since he’d hired her on. It was hard to think of Dr. William Dillon Gaster as being young, but every so often it did come to her mind just what he was, and it always threw her. As the only member of his race that didn’t simply disappear into seclusion when the war broke out, there weren’t many available points of comparison. He claimed, often with a sheepish look, to be “only” 85, and initially resisted King Asgore’s attempts to bring him on as the lead Royal Scientist. He had velvety-smooth flesh under pale skin that glowed lightly in the dark. His hair was more of a shock of white fluff that often simply seemed to have a mind of its own, and he had starry fields in the black sclera of his eyes, the irises somewhere between purple and blue with pupils like those of an octopus. Despite how alien they were, Alphys always found they were where his youth really showed. He looked at everything with at least a subtle hint of wonder, and had approached the CORE project with a giddiness that was hard to mistake. “You’re g-going to want t-to look at this.” The lizard finished, once the Doctor had finished unfolding his considerable legs from his crouch. “That’s what I was hoping you’d say.” He said, walking over. He placed a hand on her shoulder and nodded, his eyes twinkling like the roof of the Waterfall caverns. “Let’s go see what we’ve got.” “It d-doesn’t make much s-sense, is a-all.” Alphys stammered, following her boss out of the CORE. “Y-you’ll s-see.” “That’s always the exciting part!” Will exclaimed. He put his hands in his pockets, more of those summoned ones appearing to untie and remove his apron. They placed a pair of thin-rimmed glasses on his face, then tossed the apron onto a nearby table with the rest of his equipment. “The part before it makes sense!” “N-no, it. Well.” Alphys clicked her hand-claws together, then shook her head. He’d see. Will was always like this. She wondered if he’d been like this back during the war. He never talked about what he did back then. Nobody ever asked. Will hummed on the way to the research lab. Built a good extra fifty feet below the surface-level station that would eventually monitor the CORE, the research lab was a sophisticated multi-team facility that housed equipment for every discipline that the Royal Science Academy supported and then some. It even sported a communal sort of scientist barracks, a rest area for team members who couldn’t or wouldn’t leave their project too far away. And at its heart, William and his hand-picked team had been performing what he considered the most important research of their lives. Ever since the discovery that, with the right equipment, the actual structure of time could be observed on a macro scale, Will had made it his goal to oversee the project that would give them a conclusive view of it. It was beyond top-secret, the kind of research that could shake the foundations of society, and everyone working on it knew they might not like what they found. Still, Will believed he wouldn’t be much of a scientist if the potential for unpleasant results dissuaded him from carrying out a non-harmful test. He ran summoned hands through his fuzz on the elevator ride down, taking a few deep breaths. He hadn’t bothered to change out of his construction uniform, and Alphys’ eyes drifted down to stare at how he was tapping the steel toe of his boot against the wall. “Sorry.” He said, when he noticed her gaze. “Long trip down. You hear anything from Sans about his teleportation project yet? Would make this a lot simpler.” “Last I h-heard he was c-conv-vinced that he needed m-more power.” Alphys said, pushing her glasses up on her own nose. “W-wanted t-t-to wait for the C-CORE to be d-done.” “Sensible enough.” Will said. His hands fidgeted in his pockets, tracing symbols long forgotten and tapping melodies never heard against the fabric. “And has Asgore given you a budget for the robotic arm project?” “Yes!” Alphys exclaimed, and Will couldn’t decide if she sounded more surprised or relieved. “Y-yes, it’s. He d-doubled what I as-as-asked for. Couldn’t b-believe it!” “It’s a good project!” Will said, and grinned, flashing unnervingly human teeth. “You worked hard on the proposal, I’m glad to hear it! We’ll have to get you a proper work room set up.” “W-wow, my own...” Alphys trailed off, veritable stars in her eyes. “T-thank you, Will! I m-mean--” “No need for that.” Will said. Once the door opened, he marched down the hall with lengthy strides, nodding in acknowledgement to the various lab assistants and scientists that greeted him on the way. “You earned this, Doctor Alphys. Your understanding of both machinery and programming is far beyond what I could do. I can’t wait to see your results.” Alphys stammered, but managed nothing more than vague and overexcited starts at more thanks. Will beamed. She’d been barely capable of speaking at all when he brought her on three years ago to help work on the CORE project, and since then, the fresh-faced college graduate had become one of his closest partners on what he’d called Chronos Project. In her spare time, she’d built a prototype robotic arm from literal scrap, and at his urging had developed it into a proper research proposal. Perhaps once he was done with the initial Chronos results, he would discuss whether she’d be interested in picking up some interns from the Royal University of the Sciences in New Home. He pushed those thoughts aside and stepped up to the single most secure door in the Underground. Rather than presenting a hand or his face, he pressed his chest to the scanner, and sharply inhaled as it scanned his SOUL directly. It wasn’t functionally dissimilar to the common ‘Check’. But there was something about the machine that still made it uncomfortable for him. Perhaps it was the warmth of the scanner. Once the door finished unbolting itself, he stepped inside with Alphys at his heels. The control room for Project Chronos was illuminated almost entirely by a series of twelve monitors, arranged 6x2 across the back wall. Each one was magical tech, same as most of the lab equipment, and Will preferred his screens that way. At the console sat two of his other team members. Both of them snapped their heads up as he entered, and he nodded to them. “As you were. What’ve we got?” Tenor, an armless lizard with light grey scales, gestured at monitor 3 with her tail. It showed timestamps in a format Will had invented, relative to a fixed point in time that they’d identified as occurring within a day of the results coming in. “Lookin’ like some relevant events, boss. But the numbers are fucked.” Tenor had endeared herself to Will as a Junior Scientist working on Soul research, one of Will’s original passions. When she started postulating theories about the power of the soul to affect the flow of time, it wasn’t just her crass language that caught Will’s attention. He’d brought her in to look at some of Chronos’ preliminary test structures, she’d improved them immediately, and he’d worked with her on it ever since. Will cleared his throat, then leaned in to look. Sure enough, he had to admit that they didn’t look right. There was a logged disruption over a hundred years in the future relative to their point, several in the proximity of that point, three trailing behind where they currently were. He quirked his mouth. “The hell...” “Timeline chart will be had in two minutes.” Said his other team member. A male spider monster with a yellow and black carapace and eight eyes that reflected the monitors, Jacob had been a valuable member of the team from the instant Will read his paper on time-space data analysis and representation. It was supposed to be a paper on gravitation for a freshman physics class. Jake had been pulled from his classes within a month and placed on Will’s team, and through the course of the next six months of work, he’d earned the right to participate in Chronos by impressing Will beyond his years. “Let’s get ready for that data, then.” Will said, sliding his work coat off and cracking the knuckles on a pair of summoned hands. He took a seat between the pair, and Alphys pulled a chair over to sit beside Jake. “Tenor, everything vetting properly?” “Hate t’admit, boss, but yeah. Hardware an’ software both workin’ as expected. It ain’t our tech. That data’s real.” Tenor said, clawed summoned fingers dancing across her keyboard. “Did five tests while Alphy was gettin’ ya.” “Well done. Damn. Jake?” Will asked, summoning a keyboard and plugging in to monitor 6. His summoned hands started typing, more restrained than Tenor’s rapid-fire commands. “The tests will have had to be adjusted for parameters I had been believing were out of range.” Jake explained. To his credit, he sounded more intrigued than upset, and Will thanked the stars for that. “One minute to be remaining.” Will steepled his summoned fingers in front of his face, focusing on Jake’s screen. Even as new data constantly flowed across some of the other screens, he squinted through his glasses at the empty grid, waiting for the information he so badly craved. “Output is to be now.” Jake said. All eyes fell on the grid. For a full two minutes, there was silence. Will stood, his mouth agape. Alphys dropped the keyboard she was using. Jake leaned forward on the counter that held the physical keyboards, and Tenor slid back in her chair with wide eyes. “What in the absolute balls.” Will breathed, pulling his right hand from his pocket and tracing the loop on the screen. “That should be impossible.” “Even in my fuckin’ crazy talk theory thoughts I never figured there could be somethin’ like that.” Tenor agreed. “Fuckin’ stars, Will.” There on the screen, the red line of time’s flow stretched far into the future. Then it doubled back, a perfect loop that led directly backward to well before their current date. It then curved back again. And, in both directions of the loop, the path wavered badly as it approached... “Nine fifty-six in the evening, tomorrow.” Will muttered, his finger hovering over that spot. “What the hell happens tomorrow night?” “There also seems to have been something else.” Jake said, pointing. There, scattered throughout the grid, but particularly notable at the very edge of the forward part of the first iteration, the team could just barely make out the presence--the very edge--of what Will could only describe as another line. “S-s-s-separate t-t-t-t-timelines?” Alphys stammered, rubbing her forehead. “Multiple universes, maybe?” Will asked the room, squinting at those rare contact points. “Can’t be us.” Tenor confirmed. “Else we’d see the whole thing.” “It is not having been signal noise.” Jake said, looking at his work screen again. “Having had signal noise eliminated for months.” Will pursed his lips, slowly sitting back down with his hands in his pockets again. He stared at the screen for a minute longer, then exhaled long and low and loud. “Well.” He said, and paused. Closed his eyes to think for a moment, then opened them to look at his team. “Looks like we have plenty more work to do.”
1 note
·
View note
Text
Week 3 in Lund and Other Places!
Hello again from Lund, Sweden! This last week has been a wonderful touristy blur, so I think I will let the pictures speak mostly for themselves (although I am limited to only 10 I'm afraid). Saturday was visits to Lund's Kulturen open air museum, the Skissernas Museum of Sketches (pictured below), and the Cathedral which was built in the 1100's and still stands in the town's center! The University Library was also a can't miss in terms of beautiful architecture.


The next day was swimming at Lomma Beach just a bus ride away (through flower fields!) from Lund. The water wasn't too cold, but we learned too late it's common to take a sauna near the piers of the area before jumping in the waves.


This week, week number three, was the first week I have felt settled into my daily research routine. We are even starting to get some data from our isothermal calorimetry experiments to analyze! I also finally feel like I know my way around the city on foot (more or less) and was able to find some nice bakery spots. My favorite so far has been a kanelbullar, a kind of Swedish cinnamon bun, from The Patisseriet.

On Wednesday, I visited my distant relative in Copenhagen. The picture on the bottom left is the view from the top of The Church of Our Savior which, at around 90 meters or 300 feet tall with only a railing separating us from the drop at the top of the spiral, was a bit terrifying. We survived, and after making it to the bottom, had a nice dinner where we chatted about our shared family and how our lives might have been different if our parents or grandparents or great grandparents had immigrated to somewhere other than the United States and Canada or not at all. In a way, the experience was a little like a blind date. I wasn't sure what to expect going in, but it was so cool to make such a connection with family living halfway around the world.




Back in Lund at the end of the week, our class had a seminar on Swedish societal structures. I learned university tuition is free for all Swedish residents (although students have to pick an educational path much earlier because distribution requirements for majors like engineering usually aren't as common). I also learned that parental leave from work is 16 months and expected to be shared between parents where in the United States it can be as low as 3 months which is wild. My specific topic was the recycling system in Sweden and the main difference between Sweden and the U.S. is that only 1% of waste in Sweden ends up in landfills. A lot of waste is burned in energy recovery facilities which have their own issues, but there are also efforts towards circular economy like incentives for producers to make products that can be broken down at the end of their life cycle and H&M's TreeToTextile initiative to make jeans and other fabrics from cellulose.

This troll sculpture made out of scrap wood by artist Thomas Dambo who travels all over the world is of the same kind I saw when I visited Maine's botanical gardens last spring. I was surprised when I stumbled upon it around a corner in Copenhagen, but it was nice to see yet another connection to home.
I don't think this week's craziness will slow down anytime soon. Lundakarnevalen started Friday, and with parades and concerts and the like happening all weekend, I'm sure I will have lots of adventures to tell you about next week. Stay tuned!
Reegan Ketzenberger
Materials Science & Engineering
Undergraduate Research Program at Lund University: Lund, Sweden
1 note
·
View note
Photo

1:72 SAAB OAS 41 'Víðarr'; aircraft "23 Grey" of Skaraborgs Flygflottilj F 7, Swedish Air Force; Satenäs AB, 2014 (Whif/kit conversion) by dizzyfugu https://flic.kr/p/pAFA59 +++ DISCLAIMER +++ Nothing you see here is real, even though the conversion or the presented background story might be based historical facts. BEWARE! Some background: The Víðarr (or Vidar, "Wide ruler", a Nordic god among the Æsir associated with vengeance) or officially SAAB OAS 41 is Sweden's first manned aircraft with stealth technology, and the first aircraft of its kind in Europe in operational service. "OAS" is an abbreviation of the aircraft's primary tactical roles: "Osynlig Attack Spaning", "Unseen attack and reconnaissance missions". Much of the OAS 41's technology and elements were developed and tested on unmanned vehicles, namely SAAB's SHARC and FILUR demonstrators. SHARC (Swedish Highly Advanced Research Configuration) was an experimental unmanned aerial vehicle (UAV) built by Saab AB. Since the late 90-ies SAAB had been carrying out preliminary studies about several Unmanned Aerial Vehicles (UAV) concepts but not taking them into flying demonstrators. In 2001 it was decided to start the SHARC Technology Demonstrator (SHARC TD) project. Because of a limited budget and good in-house experiences from flight tests of instrumented sub-scale aircraft, it was decided that the SHARC TD should be in 1:4 scale of the original SHARC design. One of the major goals of the project was to test the airworthiness process for a military UAV or aircraft of similar layout, and this could well be achieved even with sub scaled aircraft. Even the goal of testing a lean development process for demonstrators could be achieved in that way. The SHARC TD project was initiated in 2001 with first flight less than one year later, on February 11th 2002, with the basic version. The more advanced version made its maiden flight on April 9th 2003, less than two years after project start. In September 2003 the SHARC flew a number of missions out of visual range, ranging around 20 km from the control station location. In January 2004 the effort towards the development of the ATOL functionalities was initiated, and led to a successful flight test campaign in August 2004, during which fully autonomous mission were demonstrated, from standstill to standstill. The SHARC system was composed by two flying demonstrators (BS-001 and -002), a GCS and some GSE for engine start and cooling air supply on ground. The SHARC TD is a 60 kg jet-engine driven aircraft. The airframe was manufactured in light-weight composite materials; the airframe weighed only 8 kg (without landing gear). The payload consisted of a forward looking colour video camera. The avionic system (hardware and software) was designed and manufactured by SAAB and is based on Flight Test Instrumentation system COMET 15 used in the Gripen and Viggen fighter a/c. Before the decision to develop an in house avionic system, a market survey was conduced, but no existing system had been fulfilling specifications. Electro-optic fibres, or “fly-by-light”, were used to the actuators in order to minimize the risk for Electro Magnetic Interference. Saab and FMV’s technology demonstrator program FILUR made its first flight in 2006. FILUR’s main objective was to show the tactical importance of stealth technology applied on aerial vehicles, to gain experience and to set a foundation for stealth requirements for future aerial systems and air-surveillance systems. The focus with the FILUR program was on low signature, for both radar and IR-signature. “Static measurements of radar cross section (RCS) made late 2004 showed really good performance and corresponded with calculated data. In flight measurements of stealth performance will be done as a next step”, said Jan Boström FILUR Project Manager, Saab Aerosystems. The technology developed in FILUR would be used for future Saab systems, being UAVs or manned aircraft, which became the OAS 41 which had been under development since 2004. The SAAB OAS 41 made its maiden flight in 2012, and in early 2014 a pre-production batch of five aircraft has been assigned to Skaraborgs Flygflottilj ("Skaraborg Air Force Wing") F 7 in Satenäs, where the aircraft are operated alongside JAS 39 Gripen multi-purpose fighters for evaluation and integration. Conceptually the OAS 41 is very similar to the much earlier US-American F-117, dedicated to ground attacks with precision weapons, attacks against coastal/sea targets and reconnaissance missions. All ordnance or equipment is carried internally in a large bay which is covered by sliding doors. Typical weapons include up to three Rb 75 (AGM-65 Maverick) missiles, two GBU-12 laser-guided smart bombs or two AGM 119 "Penguin" anti-ship missiles. Iron or cluster bombs as well as pods with unguided missiles are also an option. Beyond that, the aircraft can also carry air-to-air missiles like the actice radar RB 99 (AIM-129 AMRAAM) or the IR-guided Rb 74 (AIM-9L Sidewinder), up to four of each. The OAS 41 does not feature an internal gun, even though up to two podded Mauser BK 27 cannons can be carried internally. Overall, its range of weapons is highly identical to what the JAS 39 Gripen can deploy. Alternatively to offensive loads, the OAS 41 can carry camera of sensor pallets in its belly, making it highly adaptable. It is uncertain how many aircraft wil actually be built, since the Swedish Air Force officially announced that the OAS 41 is not to replace its JAS 39 fleet, rather complement it or take over exclusive missions due to its stealth features. The type's limited performance will probably confine to a limited scope of missions, and with the running cost reductions it is not expected that more than 30 OAS 41's will ever leave the production line for the Swedish Air Force, unless it would be exported and follow in the Gripen's footsteps, but this remains doubtful. General characteristics: Crew: 1 Length: 6.70 m (21 ft 11 in) Wingspan: 18,29 m (59 ft 11 in) Height: 3,96 m (13 ft) Wing area: ~68 m² (729 ft²) Empty weight: 6.739 kg (14.844 lb) Internal fuel: 2.500 l Max. takeoff weight: 13.600 kg (29,760 lb) Powerplant: 2× Svenska Flygmotor RM13S turbofans (General Electric CF34-3S), with 4.150 each Performance: Maximum speed: 692 mph (1.115 km/h) at height Cruise speed: Mach 0.7 Landing speed: 210 km/h Range: 4.828 km (3.000 mi) with internal fuel Service ceiling: 13.381 m (43.830 ft) Rate of climb: 60 m/s (11.811 ft/min) Armament: Up to 3.000 kg of ordnance, all carried in a ventral bomb bay, including air-to-ground and air-to-air missile, smart and iron bombs, gun and rocket pods, ECM equipment and pallets with cameras and sensors for reconnaissance missions. The kit and its assembly: This stealth aircraft is basically a scale-o-rama project: it is a Dragon B-2 bomber in 1:200 scale turned into a 1:72 scale aircraft. What sounds easy is more complex than it appears: you need a cockpit with a proper canopy, the landing gear has to be adjusted and there are many small details that need attention. For the cockpit installation I decided to implant a complete X-32 section from a Revell kit, it replaces the complete B-2 spine. It appears a bit bulgy, but upon close inspection of the potential internal layout I found that you can either have a flush canopy OR a bomb bay. Since I wanted to keep the latter (and enlarged it), the cockpit went a bit higher. As a result, the original X-32 canopy looked much to bulbous, it was way too high. Searching through the spares pile I eventually turned up an old F-18B canopy, which, reversed and cut into shape, could be transplanted onto the X-32's cockpit frame, even tough some sculpting at the rear was necessary. Since the F-18 canopy had some glue stains I had to sand and polish it, and as a final coat I decided to apply some light brown translucent paint. Fit is not 100%, though, but it looks good now. The high cockpit necessitated some visual counter-balance at the rear. Originally I had hoped to keep the OAS 41 fin-free, but I eventually dug out a pair of F-117 fins that were cut down in length and glued to the airframe, slightly canted outwards. The landing gear is all new. The massive front strut comes from a F-117, the wheel from the X-32. The front well was enlarged, as good as possible, but it is still too short... don't lokk there closely. ;) The main landing gear struts were taken from the X-32, while the wheels come from the F-117. The wells were lengthened at the rear, so that the longer legs find enough space. The B-2's original bomb bay was cut out and replaced by a completely scratched interior that allows the carriage of a pair of laser-guided bombs, which come from the scrap box. The exhaust slits were modified, too. They were made wider, and inside a kind of ramps were added - the original 1:200 B-2 has nothing inside. For the same reason I also added light blocks, pieces of dark grey foamed plastic, inside of the air intakes and the exhausts. Finally, at the aircraft's front, some pitots were added, but that's all since the overall hull was to remain clean. Painting and markings: I originally had the plan to make this a Japanese aircraft, but then I decided to make it a (kind of) tribute to the innovative Swedish aircraft industry - the SAAB OAS was born, and it was to carry an appropriate, if not odd, paint scheme. Even though "Fields & Meadows", made popular by the Saab 37 Viggen, was an option, I did not want to copy that style. But an angular scheme appeared logical as to confuse the aircraft contours. The splinter paint scheme I eventually settled upon was vaguely inspired by Norwegian "Skjold" class coastal patrol ships, which have stealthy hulls and carry a three-colored spinter scheme in grey, sand and dark brown. Odd for a ship, one might say, but in front of the typical Norwegian rocky coastline, it is highly effective, and even on the open sea, viewed from above, it is not a bad scheme at all. The pattern was vaguely lent from the Skjold boats, and I used different tones which would IMHO be more versatile: a reddish brown (WWII French Earth Brown), Field Grey and Olive Drab, in a wraparound scheme. Together with the edgy shape of the aircraft this turned out to be pretty effective - a bit of a surprise! The rest was rather straightforward: white for the air intakes and the landing gear, the cockpit and the bomb bay were painted in Neutral Grey. The pair of internal GBU-12s was painted in light grey, a typical tone for such weapons in Swedish use witn the JAS 39 Gripen. The kit received a light black ink washing and some panel painting with lighter shades of the basic tone, just to amphasize contours and simulate some structure and acccess panels esp. in the engine area. After decal application (puzzled together, among others, from an Italeri JAS 39 Gripen) the kit was sealed with Revell's matt acrylic varnish. In the end, a rather simple whif - I am not a friend of stealth aircraft, since they are IMHO boring. The splinter scheme changes this a bit, and the high cockpit does not look that bad at all, even though the original X-32 canopy looked REALLY weird.
3 notes
·
View notes
Link
China boycotts are a warning to Western brands Dozens of Chinese celebrities have terminated contracts or said they’ll cut ties with the brands, while H&M, the world’s second largest clothing retailer, has been pulled from major e-commerce sites. Investor insight: Nike shares tumbled more than 3% Thursday on Wall Street, while Adidas sank more than 6% in Frankfurt. In London, Burberry lost more than 4%. H&M’s stock also slid nearly 2% in Sweden. The outrage was triggered by a social media post from a group linked to the ruling Communist Party, which resurfaced a statement H&M made in September about reports of forced labor in Xinjiang. State media has since targeted other major brands that have previously spoken out. Human rights groups have repeatedly accused Beijing of detaining Uyghurs and other Muslim minority groups in “re-education” camps where they’re forced to make products that find their way into global tech and retail supply chains. Recent sanctions from the United States and other Western countries over Xinjiang have sparked renewed pushback from the Chinese government, which calls the camps “vocational training centers” designed to combat poverty and religious extremism. Blowback in China against companies that have spoken out on Xinjiang may pass, according to Bernstein analyst Aneesha Sherman. Shares of H&M rose 1% in early trading Friday, while Nike’s stock is up roughly 1.5% in premarket trading. But the episode is a reminder of the challenges Western brands face as they court the immense spending power of Chinese consumers. “It’s a tough position to manage, because they can’t really back down on their [stances], but at the same time they want to make sure they don’t abandon the Chinese customer,” Sherman told me. China accounted for roughly 5% of H&M’s sales in 2019. Sherman estimates that figure grew to about 10% in 2020, as China’s economy recovered faster from coronavirus than its home market of Europe. “In a year like this, even taking a 5% haircut off the top line is a big hit when H&M is trying to recover,” Sherman said. Luxury brands like Burberry are even more exposed, she added. Burberry listed “any significant change to Chinese consumer spending habits” as a key risk to sales in its most recent annual report. Big picture: The US-China tensions that gained prominence during the Trump era haven’t gone away, with the Biden administration and allies taking a hard line with Beijing. That creates challenges for Western companies that operate in the Chinese market. “It does affect these brands,” Sherman said. Plus, weeks like this only strengthen the hand of local competitors, which are more tapped in to regional tastes and can avoid politically-generated controversy, she noted. This powerful oil lobby has changed its tune on a carbon tax The oil industry’s most powerful lobby announced Thursday that it will support setting a price on carbon for the first time, a significant shift that underlines intensifying pressure on Washington and business to tackle the climate crisis. But the devil will be in the details, my CNN Business colleague Matt Egan reports. The American Petroleum Institute laid out a series of principles that must be met before the century-old group endorses a price on carbon. Advocates of carbon pricing say it’s crucial to fighting the climate crisis, since it would accelerate efforts to curb planet-warming emissions and force investors, companies and individuals to bear the cost of pollution. But API opposed the last serious effort to impose a price on carbon in 2010. Since then, ExxonMobil, Chevron and other industry leaders have publicly backed carbon pricing — clearing the way for others to follow. “This is a pretty big deal for the industry. There is broad recognition that obviously the country has to do something on climate change,” API CEO Mike Sommers told CNN Business. “We want to be a willing partner with the Biden administration and others in Congress who are serious about taking on this challenge.” Still, there’s skepticism among climate groups that API’s change of heart will translate to its backing of meaningful legislation. “A statement of theoretical support for a market-based carbon price is a long way from agreeing to what will likely need to be strong, binding rules to limit fossil fuel usage [and] methane emission,” Dylan Tanner, executive director of InfluenceMap, a think tank focused on energy and climate change, said in a statement. WeWork is finally going public by merging with a SPAC It’s been 18 months since WeWork scrapped its plans to go public after a disastrous IPO attempt. Now the coworking space provider appears ready to try again. The latest: The Wall Street Journal was first to report that WeWork has agreed to merge with a special-purpose acquisition company, or SPAC. The merger with BowX Acquisition Corp. would value WeWork at $9 billion. That’s a fraction of the $47 billion private market valuation the company fetched previously. Remember: WeWork was plunged into crisis in 2019 as investors combed through the company’s IPO paperwork, which revealed former CEO Adam Neumann’s unchecked power and numerous potential conflicts of interest, as well as the startup’s staggering losses. The company was forced to postpone its IPO, accept a bailout from SoftBank and reconfigure its business. Now, it could raise money by tapping into the SPAC boom. In recent months, investors have raced to set up so-called “blank check” companies, which exist purely to find private companies to merge with, effectively taking them public. Details, details: BowX Acquisition Corp., which raised $420 million from investors last year, is led by Vivek Ranadivé, who founded Tibco Software and now owns the Sacramento Kings. Ranadivé will join WeWork’s board. Up next Personal income and spending data for February posts at 8:30 a.m. ET, along with a key measure of inflation. Coming next week: The US jobs report for March is a crucial economic indicator as the recovery gathers steam. Source link Orbem News #boycotts #brands #China #investing #Premarketstocks:ChinaboycottsareawarningtoWesternbrands-CNN #warning #Western
0 notes
Text
China boycotts are a warning to Western brands
New Post has been published on https://appradab.com/china-boycotts-are-a-warning-to-western-brands/
China boycotts are a warning to Western brands



Dozens of Chinese celebrities have terminated contracts or said they’ll cut ties with the brands, while H&M, the world’s second largest clothing retailer, has been pulled from major e-commerce sites.
Investor insight: Nike shares tumbled more than 3% Thursday on Wall Street, while Adidas sank more than 6% in Frankfurt. In London, Burberry lost more than 4%. H&M’s stock also slid nearly 2% in Sweden.
The outrage was triggered by a social media post from a group linked to the ruling Communist Party, which resurfaced a statement H&M made in September about reports of forced labor in Xinjiang. State media has since targeted other major brands that have previously spoken out.
Human rights groups have repeatedly accused Beijing of detaining Uyghurs and other Muslim minority groups in “re-education” camps where they’re forced to make products that find their way into global tech and retail supply chains.
Recent sanctions from the United States and other Western countries over Xinjiang have sparked renewed pushback from the Chinese government, which calls the camps “vocational training centers” designed to combat poverty and religious extremism.
Blowback in China against companies that have spoken out on Xinjiang may pass, according to Bernstein analyst Aneesha Sherman. Shares of H&M rose 1% in early trading Friday, while Nike’s stock is up roughly 1.5% in premarket trading.
But the episode is a reminder of the challenges Western brands face as they court the immense spending power of Chinese consumers.
“It’s a tough position to manage, because they can’t really back down on their [stances], but at the same time they want to make sure they don’t abandon the Chinese customer,” Sherman told me.
China accounted for roughly 5% of H&M’s sales in 2019. Sherman estimates that figure grew to about 10% in 2020, as China’s economy recovered faster from coronavirus than its home market of Europe.
“In a year like this, even taking a 5% haircut off the top line is a big hit when H&M is trying to recover,” Sherman said.
Luxury brands like Burberry are even more exposed, she added. Burberry listed “any significant change to Chinese consumer spending habits” as a key risk to sales in its most recent annual report.
Big picture: The US-China tensions that gained prominence during the Trump era haven’t gone away, with the Biden administration and allies taking a hard line with Beijing. That creates challenges for Western companies that operate in the Chinese market.
“It does affect these brands,” Sherman said. Plus, weeks like this only strengthen the hand of local competitors, which are more tapped in to regional tastes and can avoid politically-generated controversy, she noted.
This powerful oil lobby has changed its tune on a carbon tax
The oil industry’s most powerful lobby announced Thursday that it will support setting a price on carbon for the first time, a significant shift that underlines intensifying pressure on Washington and business to tackle the climate crisis.
But the devil will be in the details, my Appradab Business colleague Matt Egan reports. The American Petroleum Institute laid out a series of principles that must be met before the century-old group endorses a price on carbon.
Advocates of carbon pricing say it’s crucial to fighting the climate crisis, since it would accelerate efforts to curb planet-warming emissions and force investors, companies and individuals to bear the cost of pollution.
But API opposed the last serious effort to impose a price on carbon in 2010. Since then, ExxonMobil, Chevron and other industry leaders have publicly backed carbon pricing — clearing the way for others to follow.
“This is a pretty big deal for the industry. There is broad recognition that obviously the country has to do something on climate change,” API CEO Mike Sommers told Appradab Business. “We want to be a willing partner with the Biden administration and others in Congress who are serious about taking on this challenge.”
Still, there’s skepticism among climate groups that API’s change of heart will translate to its backing of meaningful legislation.
“A statement of theoretical support for a market-based carbon price is a long way from agreeing to what will likely need to be strong, binding rules to limit fossil fuel usage [and] methane emission,” Dylan Tanner, executive director of InfluenceMap, a think tank focused on energy and climate change, said in a statement.
WeWork is finally going public by merging with a SPAC
It’s been 18 months since WeWork scrapped its plans to go public after a disastrous IPO attempt. Now the coworking space provider appears ready to try again.
The latest: The Wall Street Journal was first to report that WeWork has agreed to merge with a special-purpose acquisition company, or SPAC.
The merger with BowX Acquisition Corp. would value WeWork at $9 billion. That’s a fraction of the $47 billion private market valuation the company fetched previously.
Remember: WeWork was plunged into crisis in 2019 as investors combed through the company’s IPO paperwork, which revealed former CEO Adam Neumann’s unchecked power and numerous potential conflicts of interest, as well as the startup’s staggering losses.
The company was forced to postpone its IPO, accept a bailout from SoftBank and reconfigure its business.
Now, it could raise money by tapping into the SPAC boom. In recent months, investors have raced to set up so-called “blank check” companies, which exist purely to find private companies to merge with, effectively taking them public.
Details, details: BowX Acquisition Corp., which raised $420 million from investors last year, is led by Vivek Ranadivé, who founded Tibco Software and now owns the Sacramento Kings. Ranadivé will join WeWork’s board.
Up next
Personal income and spending data for February posts at 8:30 a.m. ET, along with a key measure of inflation.
Coming next week: The US jobs report for March is a crucial economic indicator as the recovery gathers steam.
0 notes
Link
Have you ever been traveling and couldn't get the same shows you normally watch back home on Hulu? Or have you noticed that some websites are blocked or you can't access certain services while you're connected to different Wi-Fi networks? That's likely due to a proxy being in place.
What is a proxy server?
A proxy server, or just proxy for short, is like having another computer that your internet requests get sent to before going to the real website. It's a server that takes all of the information you've sent out, like a request to buy new shirts on H&M, and routes it through a different IP address.
That's what makes a proxy so powerful. They can make all of your internet activity appear as if it's coming from a completely different location.
Companies use them for security and network performance purposes, individuals use them for privacy concerns, and there's also some cool functionality you can tap into when using proxy servers for your internet browsing that we'll talk about later.

A proxy can be physically located anywhere. You can set up a proxy on your home computer or you can deploy one to the cloud. The main thing that matters is that the proxy has the configurations you need for the functionality you want.
Just remember that a proxy acts like a fancy IP address filter. Similar to filters, there are different kinds of proxies and they all have their specific uses.
To get started, let's talk about the most common kind of proxy and how it works, the forward proxy.
How a proxy works
When you hear or see people talking about proxies, they're most likely referring to forward proxies. These are the most common types of proxy because they easily handle what most people need. Forward proxies act as the middleman between your requests and the server you're trying to connect to.
The way a proxy works is first you make a request, for example you try to go GitHub. So you type in the URL and hit enter. With a proxy, instead of connecting you directly to GitHub with your computer's IP address, your request gets intercepted by the proxy.
Then the proxy takes your request, updates it, and sends it from its own IP address. This can completely remove your IP address and identifying information from the request to the GitHub server.
One of the ways that proxies handle changing your request is directly in the request headers it sends to the server. A proxy request can set headers like Forwarded and Via in the original request before it sends the message to the server you're trying to get information from.
Once the proxy has updated the information from your request, it will send your reformatted request to the GitHub server. That server now thinks your request has come from a different location and it will send the data you wanted back through that location.
Next the proxy takes the data from the GitHub server and does any checks it has been configured to do with that data. It could check for any malicious scripts or other security issues. Then it finally sends the data back to your computer and your page loads.
A proxy server isn't necessarily limited to one user at a time. There can be multiple people sending requests through the same proxy and they can all share the same benefits. There are plenty of reasons you might use a proxy, even if it's a shared one.
Why you would use a proxy
Now that you know what a proxy is, it's good to know some of the common use cases for them.
You can increase network security by encrypting requests ○ Prevent hackers from intercepting sensitive information ○ Block malware sites from your real network
You can lower the amount of network traffic by caching sites ○ Cache websites so that only one request to the site is made no matter how many users are on the proxy
You can control how people use the internet ○ Block specific domains ○ Monitor and log all web requests
You can get around blocks set up by companies and countries ○ Access content from a different country ○ Get around corporate firewalls
This isn't a comprehensive list of everything you can do with proxies, but I also wanted to include some of the other benefits that don't quite fall under the typical categories.
You always have cookies blocked
You always have ads blocked
You can access the deep web
It removes any search tailoring or tracking your previous searches
You can scrap data
You can do research on your competition
Different types
There are many different types of proxies that will cover just about any configuration that you can think of. Here, I'll give you a quick overview of 14 different proxy types.
Transparent proxy
Transparent proxies are the simplest kind of proxy. They pass all of your information along, but with the proxy's IP address. These proxies don't offer any kind of privacy protection.
They tell the server you're sending your request to that the request is coming through a proxy. This is enough to get you around simple IP bans. A common use for transparent proxies is setting up website filtering, like schools and companies do.
Anonymous proxy
Anonymous proxies are a commonly used type of proxy. They never pass your IP address to the website you are browsing although they will identify themselves as a proxy in the request. This helps keep your browsing activity private.
When you don't want targeted ads following you around the internet or you don't want your location attached to your request, these are some standard proxies to use. This is usually enough to get around most targeting activities, but there is still a chance that your information might be revealed.
High anonymity proxy
These proxies are the most secure type because they don't pass along your IP address and personal data and they don't identify themselves as a proxy when making requests. They also sporadically change the IP address they use for requests. That's what allows high anonymity proxies to give you the most privacy online.
The TOR browser uses this type of proxy. Since the IP address changes occasionally, that makes it extremely hard for servers to keep track of what traffic belongs to what client. If you don't want to be tracked, this is the best option.
Distorting proxy
A distorting proxy works similarly to an anonymous proxy except it passes an IP that is purposely false. It identifies itself as a proxy and uses that false IP address in requests. This is great when you want to appear as if you were in specific location.
This is useful when you want to get around specific content restrictions. It's like you get to choose the IP address you want the proxy to use.
Residential proxy
Residential proxies are proxies that use real IP addresses. That means they are the addresses of real computers. These are the best types of proxies to use because they look like regular clients to servers.
Any of the proxy types discussed so far can be a residential proxy. As long as the proxy's IP address is associated with a physical device, these types of proxies tend to be undetectable and they get around some of the geographic problems other proxy types have.
Data center proxy
These are kind of the opposite of residential proxies. Data center proxies have computer generated IP addresses that aren't attached to a real device. It's like having a proxy in the cloud.
An advantage to this kind of proxy is their speed. Usually cloud service providers have incredible internet connections that give you speeds you couldn't get otherwise. Although they would all share similar IP addresses, one server could host hundreds of data center proxies.
Public proxy
Of all the proxy types, these are the most insecure, unreliable proxies available. They can go down at any moment and many are set up by hackers to steal data. The only reason people still use them is because they are free.
While it isn't difficult to find lists of free public proxies, it is a challenge to find good ones. You never know who these proxies are hosted by and it's a huge gamble to send any of your sensitive information through one. Any number of users can be on a public proxy at any time and there's no one regulating who uses it.
Private proxy
Private proxies have some ambiguity around what they are because they're defined by the provider offering the service. This could mean your proxy can only be used by one client at a time or that your proxy needs authentication before you can use it. These are like more reliable versions of public proxies.
A private proxy can be transparent or have high anonymity, similar to some of the others above like the residential or data center proxy. This proxy type has more to do with who can connect to it than how it handles your requests.
Dedicated proxy
A dedicated proxy is like a specific type of private proxy. It just means that the proxy can't be shared by multiple clients at the same time. So only one client can connect and send requests.
This helps prevent the IP address of the proxy from getting banned by different websites and services. It's one of the ways that a proxy provider can control who has access to the proxy to make sure that it isn't being abused.
Shared proxy
These are some of the cheapest proxies available and they work similar to shared servers. Clients pool together and split the cost of the proxy and they can all access it at the same time. Shared proxies have a more complex architecture because they handle a lot of requests at the same time.
Depending on how resources are allocated on the shared proxy, requests might be slower than over your own IP address. Because it's handling multiple requests from multiple users, the configurations of these types of proxies is more critical than the others.
Rotating proxy
Rotating proxies work a little differently from the others. Every time a client connects to the proxy, a new IP address is created for it. So they never use the same IP address more than once.
Every time a client sends a request a new IP address is generated. This is how proxies like the TOR browser work to keep your anonymity. A rotating proxy provides a high level of security and privacy when combined with some of the other types.
SSL proxy
These proxies follow the same protocol as HTTPS requests. The 'S' in HTTPS means SSL which means your web requests are secure between your client and the server you're trying to get to.
That means you get even more security because all of your requests through the proxy are encrypted. Most proxies should be using this by default, but there is still a chance you'll run into some that use HTTP.
Reverse proxy
Reverse proxies are completely different from everything we've covered so far. A reverse proxy hides the IP address of a server you're trying to send a request to. When a server needs security and privacy from clients, that's when these types of proxies come in.
These proxies are great if you need to monitor access to a server for reasons like keeping clients from having unmonitored access to a database. It can also help lower traffic on the network by passing on cached information instead of making a query each time.
Proxy Services
If you've done a quick search for proxy services, you'll know that there are a lot to choose from. Not all of them are created equally, so it's important that you know what features you want from your proxy service.
Most of these services offer combinations of the proxy types. For example, you'll be able to find residential, high anonymity, SSL proxies rolled into one service. There are a few that stand out from the others so here's a list of them, but make sure you research them to see if they meet your needs.
https://smartproxy.com/
https://www.megaproxy.com/
https://whoer.net/webproxy
https://www.proxysite.com/
https://hide.me/en/proxy
https://www.kproxy.com/
https://www.vpnbook.com/webproxy
Proxy server vs VPN
If you're familiar with VPNs (virtual private networks), then you might be wondering how a proxy is different. The main difference is that a VPN secures all of your network traffic where proxies only secure your internet traffic.
Some things that VPNs secure that proxies don’t include FTP uploads or downloads and background operating system processes, like updates.
The only thing proxies and VPNs have in common is that they make your internet traffic look like it's coming from a different IP address. That is all they have in common. The way they handle this is wildly different because of what they're used for.
A proxy just passes along your internet requests, acting like a middleman. A VPN on the other hand tunnels all of your network activity down to the operating system level. Proxies are typically used by a single application like a browser or torrenting client.
Companies tend to use VPNs to let employees access corporate resources without worrying about the traffic being intercepted or recorded by an ISP (internet service provider). These are usually hosted on a physical computer somewhere on premises.
The great thing about VPNs is that they conceal everything you do. If your ISP were to get a history of your usage, it would only see that you were connected to a VPN. Nothing about your traffic would be seen. When you connect to public Wi-Fi, a VPN is the most secure choice.
With all of the benefits that come with using a VPN, there are still good reasons people choose proxies. To start with, VPNs are typically more expensive than a proxy. You also need decent computer hardware to run a VPN. The connection is usually slower than a proxy would be.
There are plenty of times when you don’t necessarily need the kind of security that a VPN offers. When you just want to mask your activities on a single application at a low cost, a proxy might be worth considering.
Benefits and risks
Now that you know everything about proxies, here's a list of some of the benefits and risks associated with using them.
Benefits
Secure and private internet browsing
Ability to get around geo-location restrictions
Better network performance
Ability to control what websites clients have access to
Many types to choose from to suit specific needs
Risks
Your requests might return really slow
Not all proxies encrypt your requests so your information could still leak out
Free or cheap proxies could be set up by hackers or government agencies
Proxies can disappear at any time
All of your requests and information always go through a third party that could be run by anyone
There are plenty more benefits and risks to using any of the proxy server types. That's why it is important to only connect to proxy servers you trust. When you are connected to a trusted proxy, the risks should have been taken into account in the configurations so you have less to worry about.
How to set up a simple proxy server
Creating your own private proxy sounds a lot harder than it is. You can make a proxy with a computer in your house that's just as secure as most proxies you can buy. It just takes some patience and a little curiosity.
On a Linux server, you can install Squid and set the configurations for the proxy you want to create. You'll be able to do things like block specific websites or require authentication before a client can connect to the proxy.
Here's a great walk through on setting up a Squid proxy on Linux: https://devopscube.com/setup-and-configure-proxy-server/
On Windows and Mac, you have the option of making a proxy server using Python and the Google App Engine. You will have to pay for the Google App Engine service, but they make it fairly affordable.
Setting up a proxy like this is a little more involved than on Linux, but here's a great walk through: https://www.hongkiat.com/blog/proxy-with-google-app-engine/
How to connect to an existing proxy
Connecting to proxies is usually a straightforward process once you know your proxy's information, like its IP address and port number. No matter what operating system you use, proxies are usually quick to set up.
Typically you'll go into your network settings and find where you can enter your proxy information. Then you should be able to connect and a web page might appear if there's an authentication step included by the proxy. Here's what it looks like on Windows and Ubuntu.
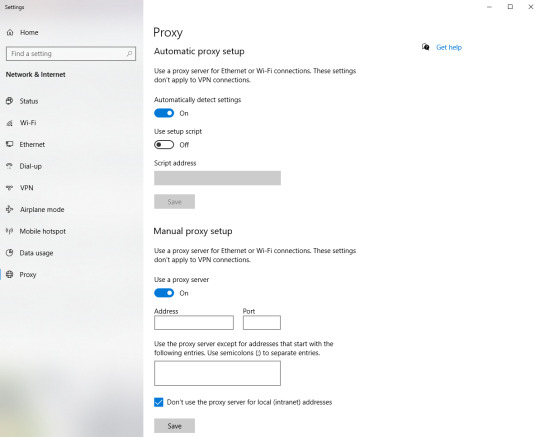
setting up a proxy server though the Windows Settings
setting up a proxy server through the Ubuntu Network Settings
Conclusion
Now you know everything about proxy servers from what they are to how to create one for yourself! I have a little proxy set up on my home network and it does make some things a lot easier to access when I'm away from home.
I write about other random stuff in tech too, like machine learning and VR. You should follow me on Twitter to learn stuff that is just cool sometimes. Plus I've got a website where you can check out my other articles and watch my slow transition from the current site to my shiny new one.
0 notes
Text
H BEAM SHOT BLASTING MACHINE
H beams shot blasting machine is the most efficient and the most effective process to remove all forms of rust and corrosion materials from h beams prior to painting or coating.
It is more efficient than steel beam shot blasting machine, steel bar shot blasting machine and scaffolding shot blasting machine. In the blasting process, use the roller conveyor system which is controlled by frequency converter to transmit h beams into the blast chamber, blast wheel throw steel shot and hit the surface of h beams, make oxide layer and dirt rust wore off quickly, after the h beam blasting, sent out from the other side.
Composition of H beam shot blasting machine: roller conveyor system, blasting chamber, abrasive recovery system, dust collector, electric control system and others.
Type
unit
QGB600
QGB1000G
QGB1500
QGB2000
QGB2500
QGB3000
Effective blasting width
mm
600
1000
1500
2000
2500
3000
Dimension of entrance(W×H)
mm
800×550
1200×550
1700×550
2200×550
2700×550
3200×550
Work speed to achieve cleaning of Sa2.5 ISO8501
m/min
0.5~3
0.5~3
0.5~3
0.5~3
0.5~3
0.5~3
Number of wheels×power
kW
4×7.5/11
4×11/15
4×11/15
6×11/15
8×11/15
8×11/15
Wheel optional
kW
—
—
—
4×15
6×15/18.5
6×15/18.5
Abrasive initial filling capacity
kg
2000
4000
4000
4500
6000
6000
Processed length of the workpiece
mm
1200~12000
1200~6000
1200~12000
3000~12000
2400~12000
3000~18000
Foundation pit required
No
No
No
Yes
Yes
Yes
The technical data is not binding and may be subject to change. Depending on the type of parts, production method, etc., further machine types and measurement specification sheets upon request.
Abrasive recovery system:
H beams shot blasting machine system use a longitudinal screw conveyor to reclaim the used blasting media and contaminants into the crosswise screw conveyor, then into the bucket elevator and abrasive residue separator, and then the cleaned abrasive get into the storage hopper to recycle, the residual will get out of the recycling system from the air wash cleaner system.
Screw conveyor
The material of the screw conveyor is 16Mn, strong wear resistance.;
Screw conveyor is first welding and then processing, to ensure the concentricity of the screw conveyor.
screw conveyor two ends adopt labyrinth type superposition seal, high self-sealing performance, resistance to high pressure.
On the below of the screw conveyor has s manual emptying valve. If the screw conveyor is blocked, it can open the emptying valve to clear the abrasive that to run the machine as soon as possible.
Abrasive residue separator
Our patented abrasive cleaner is applied for recycling shot/grit, which is to ensure high quality blasted surface and minimal abrasive shot. As the abrasive is so durable it is able to be recycled hundreds of times, resulting in an extremely low abrasive breakdown rate.
Critical to achieving this efficiency is the effectiveness of the abrasive recycling plant. Poorly designed or manufactured abrasive recycling systems will not correctly recycle the abrasive and are unable to maintain the correct abrasive working mix.
Our patented abrasive separator consists of an extended rotary separator drum that will totally remove all big clumps including big wast, scrap and paint chips etc. The abrasive is then fed through a gravity air wash separator where all dust, degraded abrasive and waste is drawn out of the good abrasive by an air current.
Only good, correctly sized abrasive is fed back to the abrasive storage hopper and blast pots for recycling.
Our patented abrasive cleaner ensures maximum recycling rates of the abrasive and high-quality surface finishing is achieved.
https://www.shotblastpro.com/products/h-beam-shot-blasting-machine.html

0 notes
Text
WARNING! Major Crypto Defi Hack Are You Safe? Bitcoin Price Holding Strong
VIDEO TRANSCRIPT
Today in crypto that queen is maintaining good price momentum as billions of dollars in stable coin sit ready to buy up the market the USA discusses yet another round of stimulus this time for a casual half trillion dollars more D. five owner abilities over the weekend have resulted in millions of dollars in crypto being stolen so I wanna make sure you know how to keep yourself safe the crypto lark this reason scrap all of the hottest of the latest happening out there in the wild wild land of crypto by the way if you are new to crypto currency and you still need help figuring out all of the basics like how to buy bitcoin how to send bitcoin has store bit coin and how to successfully investing crypto currencies in general then check out my course is called crypto currency explained this course walk you through all of those topics and more with step by step tutorials in critical resources everything you need to get started in one place that I haven’t spent a lot of time running around the internet trying to piece everything together there’s a link in the description where you can learn more so a quick peek at the charts here to get started off with today it is very nice to see bitcoin on the daily maintaining above the fifty day moving average it’s a very nice spot for bitcoin holdings here will really continue to reinforce that bullish narrative that is starting to be created in the market right now a drop below that line around the sixty nine hundred dollar mark there could set us up for a bit of a loss of faith in that bullish narrative and let the bears back out looking at the exponential moving averages the price is currently struggling with the fifty day EMA so let’s see if bitcoin can actually make a definitive close above this line on the daily before we really start that journey upwards across over the one hundred day EM. Hey around seventy five hundred and then of course the two hundred day E. M. A. at around eight thousand dollars which is also where the two hundred day standard moving averages if we can get across these lines and really just close a definitive couple of candles above those two hundred day moving averages and I would say that we are back in business and it will be on to bowl season once again until then though I do appreciate the Kerr momentum but take it all with a grain of salt nice though to see bitcoin maintaining a solid uptrend on the daily currently as well and of course the weekly just closed for bitcoin giving us our fifth green candle in a row which is definitely nice to see the general momentum in the market has definitely been encouraging it is really I think getting people excited about that bullish narrative again but do remain aware of the wider risks to the global economy right now and that the crisis is far from over so still a wild cards can be pulled out here but a bit of hope you could come in the form of stablecoin accumulation on exchanges right now cryptocurrency exchanges are holding over three billion dollars in stable coins on behalf of their customers showing that traders and investors are essentially sitting with just loads of cash ready to be deployed into the markets yeah sure a percentage of this is just the traders moving in and out of the markets but a good amount of that will be those who are waiting to either bite in up coming dip or perhaps waiting for further confirmation that the bulls are indeed back in charge of the markets before and during their long term plays three billion dollars that’s a lot of chatter man a lot of chatter and when that money starts moving back into bitcoin it could have a very dramatic effect on the price pushing the market’s very high very fast but. When it comes to having lots and lots of chatter no one does it quite like America they remember on Friday in our office so how is saying that the small business stimulus loan program was already out of its three hundred and fifty billion dollar budget yeah well. Over the weekend the U. S. administration they have been discussing putting up another four hundred and fifty billion dollars in stimulus to fight the current crisis now the program would consist of three hundred billion dollars to the paycheck protection program is sixty billion dollars to separate emergency loan program for small businesses, of course, it is worth remembering that the previous three hundred and fifty billion dollars for small businesses ran out in just three weeks so how long will this current truncheon of money take to disappear not long that’s how it’ll be gone it really really fast this proposal also includes one hundred billion dollars for hospitals and for testing for the virus so. Is this money needed for these purposes I have no doubt that it is and obviously you know these people should be helped these businesses should be helped hospital should help all that I’m not disagreeing with the idea of spending all this money the question now is where is that money coming from was the long term impact of that you see this is another half trillion dollars in just one week and one week that money does not come from a magical savings account or from selling gold from Fort Knox or something like that no no no no no just type in it into the computer that’s that magic money just appears that’s how they do it that’s how they do it it’s crazy massive inflation could be coming for the dollar and well bit coin may not have done very well in the short term of this liquidity crisis that sparked back in March long term we will see bit queen shining as the inflation crisis starts the heat up there is no way that all this data in money supply expansion is going to happen without hurting the dollar in the long term. Now on to the main theme of today’s video keeping your crypto safe the first is about storage risks for your bitcoin so a longtime community member with actually robbed the other day he shared a story it’s terrible what happened to him while he was away from home someone climbed on whose balcony came in through his door stole his laptop in a still a framed piece of art on his wall that contained his one and only bitcoin paper wallet. All the bitcoin that has been diligently stacking for three years and there was no copy I just it’s a devastating story I’m just so sorry here’s happens god in such a big community supporter for the last few years he just a good dude and it’s just a tough situation but I really want to take just a minute to tell the story because it’s just such an important reminder to take your security of your crypto just incredibly seriously always remember the best practices when it comes to store your bitcoin paper wallet for example on the one hand they are quite safe on the other hand there just paper and that paper get wet or eaten by dog or stolen so you know it’s not a perfect solution of course entering that private he later on to retrieve your bitcoin also be tricky hardware wallets they remain the most effective in the safest way for the average user to safely store their crypto if you do not yet have a hardware wallet then please consider getting one is the safest way for the average user tips successfully store their crypto whether you choose a paper or a software or a hardware wallet always maintain the best practices right down in keep at least two copies of your keys or your passphrase and always do this using pen and paper laminated if you can of course rent water damage as well and then take those copies and put them in different places very simple stuff here are very important make sure you put it somewhere completely just not obvious and something in which a thief would never consider taking like Jane Austen book or something like that never store your keys online either you have a high risk of losing your crypto if you do your crypto can be gone in an instant if you don’t properly secure it if you do need a hardware wallet then ledger currently has an. Awesome sale going on we can actually get a family pack or a backup packs you can get yourself a whole big pile ledgers not me personally I always have multiple devices on hand collection Animax ledger nano S. and dental X. in the box this is just in case I lose water in case one of these devices get stolen and I can just take my passphrase set it up on the new device and I’m back in business a past Fraser had an incredibly secure and hard to find places so I feel quite comfortable about my back up for my security and of course either someone actually does steal your ledger wallet it just resets after three failed log in attempts so it’s very very secure the device is a very good place to keep your crypto there’s a link down below we can get yourself a ledger and also include a video tutorial for the ledger which will actually answer many of the common questions that people seem to have about using one of these devices please please please take your security seriously all of your years of stacking stats can be invalidated in a minute of crime so please take it seriously and finally the big story of today is that over the weekend a number of major decentralized finance exploits have happened to someone took advantage of the known exploit in the E. R. C. seven seven token standard to steal three hundred thousand dollars in Ethereum and wrapped a bit coin from a unique swap tokom pool there’s also been a critical vulnerability which has been found by the curve team in the synthetics S. U. S. D. contract now the vulnerability was found before anything bad happened all the funds are safe there has been no lost the vulnerability is currently being fixed actually the team has done really well here to act proactively to prevent any exploits of that vulnerability from happening this is why using H.. Rusted professional decentralized finance application like synthetics is so important in the first place because you have people working actively on the development of that product which you can trust but the big one of the weekend has to be this one lending protocols land F. dot and he was happy for twenty-five million dollars in crypto. The hacker drain basically all of the funds on the platform so this graph here you can see so eloquently illustrates how quickly the crypto disappeared from this platform and the hackers in a very savage follow up even sent a few thousand dollars worth of taxes tokens back to the team with a little note attached on the blockchain better future burn man that hurts yes split was again a known attack vector that took advantage of the known smart contract vulnerability now lend F. dot M. eat came under a lot of criticism actually hasn’t actually deployed and then apparently bastardized compound finances copyrighted code without consent and more critically it is apparent that the codes thieves not only lack the knowledge to develop their own smart contracts but they also lack the knowledge to properly maintain the smart contracts in to know how to audit for security vulnerabilities twenty five million Bucks in crypto gone. Just like that if there is a back door the hackers will find it there is no stopping and it’s their full-time job this is what they do but this for me just underlines that. It’s important to understand the risks remain in the decentralized finance space which is why for most people lending with someone like block fight for getting involved in lending is a much better option than landing on a lot of these decentralized markets however if you are going to be using a decentralized finance product then there are some things to keep in mind that you can use to keep yourself safe first off only use trusted and well established providers I’m talking the likes of kybernetwork and synthetics and compound finance their teams that have proven that they have what it takes to stay ahead of the curve to find vulnerabilities before the bad guys do into fix that maybe really really proactive about their code bases of course never risk more than you can afford to lose on the fight either we are still in the early experimental stages of this technology mistakes will happen money will be lost also use insurance on your defy plays if you can’t companies like nexus mutual actually offer you the chance to ensure your funds against smart contract failure but they do not insure all companies so be very wary of new players like land after dot M. E. that are entering the market many of these guys they’re gonna be fly by night types of operations just riding the defy hype wave. More money will be lost in the fi you can count on it that being said I remain incredibly optimistic about the future of decentralized finance early adopters of this technology they’re taking risks that the rest of us can sleep easy in the future but if you are not up for the risks of decentralized finance or you do not understand the risks thing keep your bitcoin or your theory I’m just locked up on your ledger or if you do want to get into the lending market use a service like block fi they’re highly regulated highly compliant a lot saved a lot of these defy platforms but long term this technology layer which we see being built on open public networks like Ethereum will be fundamental in challenging the existing financial order and then massively disrupting it so I remain very bullish on the future of the fight your question for today what are you doing to keep your cryptocurrency secure in are you using any defy applications and if so do you fully understand the risks that you are taking would love to know down below in the comments section what you are doing to keep your crypto safe thank you so much watching today’s video massively appreciate as always the time to take a few days over here and watch this did talk about crypto currencies on the internet seriously none of this is possible values thank you so much and enjoy today’s video hit that thumbs up button make sure to subscribe to the channel if you are new around here long live the blockchain. Add the peace out the next time.
Via https://www.cryptosharks.net/major-crypto-defi-hack-are-you-safe/
source https://cryptosharks.weebly.com/blog/warning-major-crypto-defi-hack-are-you-safe-bitcoin-price-holding-strong
0 notes
Text
WARNING! Major Crypto Defi Hack, Are You Safe? Bitcoin Price Holding Strong
VIDEO TRANSCRIPT
Today in crypto that queen is maintaining good price momentum as billions of dollars in stable coin sit ready to buy up the market the USA discusses yet another round of stimulus this time for a casual half trillion dollars more D. five owner abilities over the weekend have resulted in millions of dollars in crypto being stolen so I wanna make sure you know how to keep yourself safe the crypto lark this reason scrap all of the hottest of the latest happening out there in the wild wild land of crypto by the way if you are new to crypto currency and you still need help figuring out all of the basics like how to buy bitcoin how to send bitcoin has store bit coin and how to successfully investing crypto currencies in general then check out my course is called crypto currency explained this course walk you through all of those topics and more with step by step tutorials in critical resources everything you need to get started in one place that I haven’t spent a lot of time running around the internet trying to piece everything together there’s a link in the description where you can learn more so a quick peek at the charts here to get started off with today it is very nice to see bitcoin on the daily maintaining above the fifty day moving average it’s a very nice spot for bitcoin holdings here will really continue to reinforce that bullish narrative that is starting to be created in the market right now a drop below that line around the sixty nine hundred dollar mark there could set us up for a bit of a loss of faith in that bullish narrative and let the bears back out looking at the exponential moving averages the price is currently struggling with the fifty day EMA so let’s see if bitcoin can actually make a definitive close above this line on the daily before we really start that journey upwards across over the one hundred day EM. Hey around seventy five hundred and then of course the two hundred day E. M. A. at around eight thousand dollars which is also where the two hundred day standard moving averages if we can get across these lines and really just close a definitive couple of candles above those two hundred day moving averages and I would say that we are back in business and it will be on to bowl season once again until then though I do appreciate the Kerr momentum but take it all with a grain of salt nice though to see bitcoin maintaining a solid uptrend on the daily currently as well and of course the weekly just closed for bitcoin giving us our fifth green candle in a row which is definitely nice to see the general momentum in the market has definitely been encouraging it is really I think getting people excited about that bullish narrative again but do remain aware of the wider risks to the global economy right now and that the crisis is far from over so still a wild cards can be pulled out here but a bit of hope you could come in the form of stablecoin accumulation on exchanges right now cryptocurrency exchanges are holding over three billion dollars in stable coins on behalf of their customers showing that traders and investors are essentially sitting with just loads of cash ready to be deployed into the markets yeah sure a percentage of this is just the traders moving in and out of the markets but a good amount of that will be those who are waiting to either bite in up coming dip or perhaps waiting for further confirmation that the bulls are indeed back in charge of the markets before and during their long term plays three billion dollars that’s a lot of chatter man a lot of chatter and when that money starts moving back into bitcoin it could have a very dramatic effect on the price pushing the market’s very high very fast but. When it comes to having lots and lots of chatter no one does it quite like America they remember on Friday in our office so how is saying that the small business stimulus loan program was already out of its three hundred and fifty billion dollar budget yeah well. Over the weekend the U. S. administration they have been discussing putting up another four hundred and fifty billion dollars in stimulus to fight the current crisis now the program would consist of three hundred billion dollars to the paycheck protection program is sixty billion dollars to separate emergency loan program for small businesses, of course, it is worth remembering that the previous three hundred and fifty billion dollars for small businesses ran out in just three weeks so how long will this current truncheon of money take to disappear not long that’s how it’ll be gone it really really fast this proposal also includes one hundred billion dollars for hospitals and for testing for the virus so. Is this money needed for these purposes I have no doubt that it is and obviously you know these people should be helped these businesses should be helped hospital should help all that I’m not disagreeing with the idea of spending all this money the question now is where is that money coming from was the long term impact of that you see this is another half trillion dollars in just one week and one week that money does not come from a magical savings account or from selling gold from Fort Knox or something like that no no no no no just type in it into the computer that’s that magic money just appears that’s how they do it that’s how they do it it’s crazy massive inflation could be coming for the dollar and well bit coin may not have done very well in the short term of this liquidity crisis that sparked back in March long term we will see bit queen shining as the inflation crisis starts the heat up there is no way that all this data in money supply expansion is going to happen without hurting the dollar in the long term. Now on to the main theme of today’s video keeping your crypto safe the first is about storage risks for your bitcoin so a longtime community member with actually robbed the other day he shared a story it’s terrible what happened to him while he was away from home someone climbed on whose balcony came in through his door stole his laptop in a still a framed piece of art on his wall that contained his one and only bitcoin paper wallet. All the bitcoin that has been diligently stacking for three years and there was no copy I just it’s a devastating story I’m just so sorry here’s happens god in such a big community supporter for the last few years he just a good dude and it’s just a tough situation but I really want to take just a minute to tell the story because it’s just such an important reminder to take your security of your crypto just incredibly seriously always remember the best practices when it comes to store your bitcoin paper wallet for example on the one hand they are quite safe on the other hand there just paper and that paper get wet or eaten by dog or stolen so you know it’s not a perfect solution of course entering that private he later on to retrieve your bitcoin also be tricky hardware wallets they remain the most effective in the safest way for the average user to safely store their crypto if you do not yet have a hardware wallet then please consider getting one is the safest way for the average user tips successfully store their crypto whether you choose a paper or a software or a hardware wallet always maintain the best practices right down in keep at least two copies of your keys or your passphrase and always do this using pen and paper laminated if you can of course rent water damage as well and then take those copies and put them in different places very simple stuff here are very important make sure you put it somewhere completely just not obvious and something in which a thief would never consider taking like Jane Austen book or something like that never store your keys online either you have a high risk of losing your crypto if you do your crypto can be gone in an instant if you don’t properly secure it if you do need a hardware wallet then ledger currently has an. Awesome sale going on we can actually get a family pack or a backup packs you can get yourself a whole big pile ledgers not me personally I always have multiple devices on hand collection Animax ledger nano S. and dental X. in the box this is just in case I lose water in case one of these devices get stolen and I can just take my passphrase set it up on the new device and I’m back in business a past Fraser had an incredibly secure and hard to find places so I feel quite comfortable about my back up for my security and of course either someone actually does steal your ledger wallet it just resets after three failed log in attempts so it’s very very secure the device is a very good place to keep your crypto there’s a link down below we can get yourself a ledger and also include a video tutorial for the ledger which will actually answer many of the common questions that people seem to have about using one of these devices please please please take your security seriously all of your years of stacking stats can be invalidated in a minute of crime so please take it seriously and finally the big story of today is that over the weekend a number of major decentralized finance exploits have happened to someone took advantage of the known exploit in the E. R. C. seven seven token standard to steal three hundred thousand dollars in Ethereum and wrapped a bit coin from a unique swap tokom pool there’s also been a critical vulnerability which has been found by the curve team in the synthetics S. U. S. D. contract now the vulnerability was found before anything bad happened all the funds are safe there has been no lost the vulnerability is currently being fixed actually the team has done really well here to act proactively to prevent any exploits of that vulnerability from happening this is why using H.. Rusted professional decentralized finance application like synthetics is so important in the first place because you have people working actively on the development of that product which you can trust but the big one of the weekend has to be this one lending protocols land F. dot and he was happy for twenty-five million dollars in crypto. The hacker drain basically all of the funds on the platform so this graph here you can see so eloquently illustrates how quickly the crypto disappeared from this platform and the hackers in a very savage follow up even sent a few thousand dollars worth of taxes tokens back to the team with a little note attached on the blockchain better future burn man that hurts yes split was again a known attack vector that took advantage of the known smart contract vulnerability now lend F. dot M. eat came under a lot of criticism actually hasn’t actually deployed and then apparently bastardized compound finances copyrighted code without consent and more critically it is apparent that the codes thieves not only lack the knowledge to develop their own smart contracts but they also lack the knowledge to properly maintain the smart contracts in to know how to audit for security vulnerabilities twenty five million Bucks in crypto gone. Just like that if there is a back door the hackers will find it there is no stopping and it’s their full-time job this is what they do but this for me just underlines that. It’s important to understand the risks remain in the decentralized finance space which is why for most people lending with someone like block fight for getting involved in lending is a much better option than landing on a lot of these decentralized markets however if you are going to be using a decentralized finance product then there are some things to keep in mind that you can use to keep yourself safe first off only use trusted and well established providers I’m talking the likes of kybernetwork and synthetics and compound finance their teams that have proven that they have what it takes to stay ahead of the curve to find vulnerabilities before the bad guys do into fix that maybe really really proactive about their code bases of course never risk more than you can afford to lose on the fight either we are still in the early experimental stages of this technology mistakes will happen money will be lost also use insurance on your defy plays if you can’t companies like nexus mutual actually offer you the chance to ensure your funds against smart contract failure but they do not insure all companies so be very wary of new players like land after dot M. E. that are entering the market many of these guys they’re gonna be fly by night types of operations just riding the defy hype wave. More money will be lost in the fi you can count on it that being said I remain incredibly optimistic about the future of decentralized finance early adopters of this technology they’re taking risks that the rest of us can sleep easy in the future but if you are not up for the risks of decentralized finance or you do not understand the risks thing keep your bitcoin or your theory I’m just locked up on your ledger or if you do want to get into the lending market use a service like block fi they’re highly regulated highly compliant a lot saved a lot of these defy platforms but long term this technology layer which we see being built on open public networks like Ethereum will be fundamental in challenging the existing financial order and then massively disrupting it so I remain very bullish on the future of the fight your question for today what are you doing to keep your cryptocurrency secure in are you using any defy applications and if so do you fully understand the risks that you are taking would love to know down below in the comments section what you are doing to keep your crypto safe thank you so much watching today’s video massively appreciate as always the time to take a few days over here and watch this did talk about crypto currencies on the internet seriously none of this is possible values thank you so much and enjoy today’s video hit that thumbs up button make sure to subscribe to the channel if you are new around here long live the blockchain. Add the peace out the next time.
source https://www.cryptosharks.net/major-crypto-defi-hack-are-you-safe/ source https://cryptosharks1.blogspot.com/2020/04/warning-major-crypto-defi-hack-are-you.html
0 notes
Text
WARNING! Major Crypto Defi Hack, Are You Safe? Bitcoin Price Holding Strong
VIDEO TRANSCRIPT
Today in crypto that queen is maintaining good price momentum as billions of dollars in stable coin sit ready to buy up the market the USA discusses yet another round of stimulus this time for a casual half trillion dollars more D. five owner abilities over the weekend have resulted in millions of dollars in crypto being stolen so I wanna make sure you know how to keep yourself safe the crypto lark this reason scrap all of the hottest of the latest happening out there in the wild wild land of crypto by the way if you are new to crypto currency and you still need help figuring out all of the basics like how to buy bitcoin how to send bitcoin has store bit coin and how to successfully investing crypto currencies in general then check out my course is called crypto currency explained this course walk you through all of those topics and more with step by step tutorials in critical resources everything you need to get started in one place that I haven’t spent a lot of time running around the internet trying to piece everything together there’s a link in the description where you can learn more so a quick peek at the charts here to get started off with today it is very nice to see bitcoin on the daily maintaining above the fifty day moving average it’s a very nice spot for bitcoin holdings here will really continue to reinforce that bullish narrative that is starting to be created in the market right now a drop below that line around the sixty nine hundred dollar mark there could set us up for a bit of a loss of faith in that bullish narrative and let the bears back out looking at the exponential moving averages the price is currently struggling with the fifty day EMA so let’s see if bitcoin can actually make a definitive close above this line on the daily before we really start that journey upwards across over the one hundred day EM. Hey around seventy five hundred and then of course the two hundred day E. M. A. at around eight thousand dollars which is also where the two hundred day standard moving averages if we can get across these lines and really just close a definitive couple of candles above those two hundred day moving averages and I would say that we are back in business and it will be on to bowl season once again until then though I do appreciate the Kerr momentum but take it all with a grain of salt nice though to see bitcoin maintaining a solid uptrend on the daily currently as well and of course the weekly just closed for bitcoin giving us our fifth green candle in a row which is definitely nice to see the general momentum in the market has definitely been encouraging it is really I think getting people excited about that bullish narrative again but do remain aware of the wider risks to the global economy right now and that the crisis is far from over so still a wild cards can be pulled out here but a bit of hope you could come in the form of stablecoin accumulation on exchanges right now cryptocurrency exchanges are holding over three billion dollars in stable coins on behalf of their customers showing that traders and investors are essentially sitting with just loads of cash ready to be deployed into the markets yeah sure a percentage of this is just the traders moving in and out of the markets but a good amount of that will be those who are waiting to either bite in up coming dip or perhaps waiting for further confirmation that the bulls are indeed back in charge of the markets before and during their long term plays three billion dollars that’s a lot of chatter man a lot of chatter and when that money starts moving back into bitcoin it could have a very dramatic effect on the price pushing the market’s very high very fast but. When it comes to having lots and lots of chatter no one does it quite like America they remember on Friday in our office so how is saying that the small business stimulus loan program was already out of its three hundred and fifty billion dollar budget yeah well. Over the weekend the U. S. administration they have been discussing putting up another four hundred and fifty billion dollars in stimulus to fight the current crisis now the program would consist of three hundred billion dollars to the paycheck protection program is sixty billion dollars to separate emergency loan program for small businesses, of course, it is worth remembering that the previous three hundred and fifty billion dollars for small businesses ran out in just three weeks so how long will this current truncheon of money take to disappear not long that’s how it’ll be gone it really really fast this proposal also includes one hundred billion dollars for hospitals and for testing for the virus so. Is this money needed for these purposes I have no doubt that it is and obviously you know these people should be helped these businesses should be helped hospital should help all that I’m not disagreeing with the idea of spending all this money the question now is where is that money coming from was the long term impact of that you see this is another half trillion dollars in just one week and one week that money does not come from a magical savings account or from selling gold from Fort Knox or something like that no no no no no just type in it into the computer that’s that magic money just appears that’s how they do it that’s how they do it it’s crazy massive inflation could be coming for the dollar and well bit coin may not have done very well in the short term of this liquidity crisis that sparked back in March long term we will see bit queen shining as the inflation crisis starts the heat up there is no way that all this data in money supply expansion is going to happen without hurting the dollar in the long term. Now on to the main theme of today’s video keeping your crypto safe the first is about storage risks for your bitcoin so a longtime community member with actually robbed the other day he shared a story it’s terrible what happened to him while he was away from home someone climbed on whose balcony came in through his door stole his laptop in a still a framed piece of art on his wall that contained his one and only bitcoin paper wallet. All the bitcoin that has been diligently stacking for three years and there was no copy I just it’s a devastating story I’m just so sorry here’s happens god in such a big community supporter for the last few years he just a good dude and it’s just a tough situation but I really want to take just a minute to tell the story because it’s just such an important reminder to take your security of your crypto just incredibly seriously always remember the best practices when it comes to store your bitcoin paper wallet for example on the one hand they are quite safe on the other hand there just paper and that paper get wet or eaten by dog or stolen so you know it’s not a perfect solution of course entering that private he later on to retrieve your bitcoin also be tricky hardware wallets they remain the most effective in the safest way for the average user to safely store their crypto if you do not yet have a hardware wallet then please consider getting one is the safest way for the average user tips successfully store their crypto whether you choose a paper or a software or a hardware wallet always maintain the best practices right down in keep at least two copies of your keys or your passphrase and always do this using pen and paper laminated if you can of course rent water damage as well and then take those copies and put them in different places very simple stuff here are very important make sure you put it somewhere completely just not obvious and something in which a thief would never consider taking like Jane Austen book or something like that never store your keys online either you have a high risk of losing your crypto if you do your crypto can be gone in an instant if you don’t properly secure it if you do need a hardware wallet then ledger currently has an. Awesome sale going on we can actually get a family pack or a backup packs you can get yourself a whole big pile ledgers not me personally I always have multiple devices on hand collection Animax ledger nano S. and dental X. in the box this is just in case I lose water in case one of these devices get stolen and I can just take my passphrase set it up on the new device and I’m back in business a past Fraser had an incredibly secure and hard to find places so I feel quite comfortable about my back up for my security and of course either someone actually does steal your ledger wallet it just resets after three failed log in attempts so it’s very very secure the device is a very good place to keep your crypto there’s a link down below we can get yourself a ledger and also include a video tutorial for the ledger which will actually answer many of the common questions that people seem to have about using one of these devices please please please take your security seriously all of your years of stacking stats can be invalidated in a minute of crime so please take it seriously and finally the big story of today is that over the weekend a number of major decentralized finance exploits have happened to someone took advantage of the known exploit in the E. R. C. seven seven token standard to steal three hundred thousand dollars in Ethereum and wrapped a bit coin from a unique swap tokom pool there’s also been a critical vulnerability which has been found by the curve team in the synthetics S. U. S. D. contract now the vulnerability was found before anything bad happened all the funds are safe there has been no lost the vulnerability is currently being fixed actually the team has done really well here to act proactively to prevent any exploits of that vulnerability from happening this is why using H.. Rusted professional decentralized finance application like synthetics is so important in the first place because you have people working actively on the development of that product which you can trust but the big one of the weekend has to be this one lending protocols land F. dot and he was happy for twenty-five million dollars in crypto. The hacker drain basically all of the funds on the platform so this graph here you can see so eloquently illustrates how quickly the crypto disappeared from this platform and the hackers in a very savage follow up even sent a few thousand dollars worth of taxes tokens back to the team with a little note attached on the blockchain better future burn man that hurts yes split was again a known attack vector that took advantage of the known smart contract vulnerability now lend F. dot M. eat came under a lot of criticism actually hasn’t actually deployed and then apparently bastardized compound finances copyrighted code without consent and more critically it is apparent that the codes thieves not only lack the knowledge to develop their own smart contracts but they also lack the knowledge to properly maintain the smart contracts in to know how to audit for security vulnerabilities twenty five million Bucks in crypto gone. Just like that if there is a back door the hackers will find it there is no stopping and it’s their full-time job this is what they do but this for me just underlines that. It’s important to understand the risks remain in the decentralized finance space which is why for most people lending with someone like block fight for getting involved in lending is a much better option than landing on a lot of these decentralized markets however if you are going to be using a decentralized finance product then there are some things to keep in mind that you can use to keep yourself safe first off only use trusted and well established providers I’m talking the likes of kybernetwork and synthetics and compound finance their teams that have proven that they have what it takes to stay ahead of the curve to find vulnerabilities before the bad guys do into fix that maybe really really proactive about their code bases of course never risk more than you can afford to lose on the fight either we are still in the early experimental stages of this technology mistakes will happen money will be lost also use insurance on your defy plays if you can’t companies like nexus mutual actually offer you the chance to ensure your funds against smart contract failure but they do not insure all companies so be very wary of new players like land after dot M. E. that are entering the market many of these guys they’re gonna be fly by night types of operations just riding the defy hype wave. More money will be lost in the fi you can count on it that being said I remain incredibly optimistic about the future of decentralized finance early adopters of this technology they’re taking risks that the rest of us can sleep easy in the future but if you are not up for the risks of decentralized finance or you do not understand the risks thing keep your bitcoin or your theory I’m just locked up on your ledger or if you do want to get into the lending market use a service like block fi they’re highly regulated highly compliant a lot saved a lot of these defy platforms but long term this technology layer which we see being built on open public networks like Ethereum will be fundamental in challenging the existing financial order and then massively disrupting it so I remain very bullish on the future of the fight your question for today what are you doing to keep your cryptocurrency secure in are you using any defy applications and if so do you fully understand the risks that you are taking would love to know down below in the comments section what you are doing to keep your crypto safe thank you so much watching today’s video massively appreciate as always the time to take a few days over here and watch this did talk about crypto currencies on the internet seriously none of this is possible values thank you so much and enjoy today’s video hit that thumbs up button make sure to subscribe to the channel if you are new around here long live the blockchain. Add the peace out the next time.
source https://www.cryptosharks.net/major-crypto-defi-hack-are-you-safe/ source https://cryptosharks1.tumblr.com/post/616133263007907840
0 notes
Text
WARNING! Major Crypto Defi Hack, Are You Safe? Bitcoin Price Holding Strong
VIDEO TRANSCRIPT
Today in crypto that queen is maintaining good price momentum as billions of dollars in stable coin sit ready to buy up the market the USA discusses yet another round of stimulus this time for a casual half trillion dollars more D. five owner abilities over the weekend have resulted in millions of dollars in crypto being stolen so I wanna make sure you know how to keep yourself safe the crypto lark this reason scrap all of the hottest of the latest happening out there in the wild wild land of crypto by the way if you are new to crypto currency and you still need help figuring out all of the basics like how to buy bitcoin how to send bitcoin has store bit coin and how to successfully investing crypto currencies in general then check out my course is called crypto currency explained this course walk you through all of those topics and more with step by step tutorials in critical resources everything you need to get started in one place that I haven’t spent a lot of time running around the internet trying to piece everything together there’s a link in the description where you can learn more so a quick peek at the charts here to get started off with today it is very nice to see bitcoin on the daily maintaining above the fifty day moving average it’s a very nice spot for bitcoin holdings here will really continue to reinforce that bullish narrative that is starting to be created in the market right now a drop below that line around the sixty nine hundred dollar mark there could set us up for a bit of a loss of faith in that bullish narrative and let the bears back out looking at the exponential moving averages the price is currently struggling with the fifty day EMA so let’s see if bitcoin can actually make a definitive close above this line on the daily before we really start that journey upwards across over the one hundred day EM. Hey around seventy five hundred and then of course the two hundred day E. M. A. at around eight thousand dollars which is also where the two hundred day standard moving averages if we can get across these lines and really just close a definitive couple of candles above those two hundred day moving averages and I would say that we are back in business and it will be on to bowl season once again until then though I do appreciate the Kerr momentum but take it all with a grain of salt nice though to see bitcoin maintaining a solid uptrend on the daily currently as well and of course the weekly just closed for bitcoin giving us our fifth green candle in a row which is definitely nice to see the general momentum in the market has definitely been encouraging it is really I think getting people excited about that bullish narrative again but do remain aware of the wider risks to the global economy right now and that the crisis is far from over so still a wild cards can be pulled out here but a bit of hope you could come in the form of stablecoin accumulation on exchanges right now cryptocurrency exchanges are holding over three billion dollars in stable coins on behalf of their customers showing that traders and investors are essentially sitting with just loads of cash ready to be deployed into the markets yeah sure a percentage of this is just the traders moving in and out of the markets but a good amount of that will be those who are waiting to either bite in up coming dip or perhaps waiting for further confirmation that the bulls are indeed back in charge of the markets before and during their long term plays three billion dollars that’s a lot of chatter man a lot of chatter and when that money starts moving back into bitcoin it could have a very dramatic effect on the price pushing the market’s very high very fast but. When it comes to having lots and lots of chatter no one does it quite like America they remember on Friday in our office so how is saying that the small business stimulus loan program was already out of its three hundred and fifty billion dollar budget yeah well. Over the weekend the U. S. administration they have been discussing putting up another four hundred and fifty billion dollars in stimulus to fight the current crisis now the program would consist of three hundred billion dollars to the paycheck protection program is sixty billion dollars to separate emergency loan program for small businesses, of course, it is worth remembering that the previous three hundred and fifty billion dollars for small businesses ran out in just three weeks so how long will this current truncheon of money take to disappear not long that’s how it’ll be gone it really really fast this proposal also includes one hundred billion dollars for hospitals and for testing for the virus so. Is this money needed for these purposes I have no doubt that it is and obviously you know these people should be helped these businesses should be helped hospital should help all that I’m not disagreeing with the idea of spending all this money the question now is where is that money coming from was the long term impact of that you see this is another half trillion dollars in just one week and one week that money does not come from a magical savings account or from selling gold from Fort Knox or something like that no no no no no just type in it into the computer that’s that magic money just appears that’s how they do it that’s how they do it it’s crazy massive inflation could be coming for the dollar and well bit coin may not have done very well in the short term of this liquidity crisis that sparked back in March long term we will see bit queen shining as the inflation crisis starts the heat up there is no way that all this data in money supply expansion is going to happen without hurting the dollar in the long term. Now on to the main theme of today’s video keeping your crypto safe the first is about storage risks for your bitcoin so a longtime community member with actually robbed the other day he shared a story it’s terrible what happened to him while he was away from home someone climbed on whose balcony came in through his door stole his laptop in a still a framed piece of art on his wall that contained his one and only bitcoin paper wallet. All the bitcoin that has been diligently stacking for three years and there was no copy I just it’s a devastating story I’m just so sorry here’s happens god in such a big community supporter for the last few years he just a good dude and it’s just a tough situation but I really want to take just a minute to tell the story because it’s just such an important reminder to take your security of your crypto just incredibly seriously always remember the best practices when it comes to store your bitcoin paper wallet for example on the one hand they are quite safe on the other hand there just paper and that paper get wet or eaten by dog or stolen so you know it’s not a perfect solution of course entering that private he later on to retrieve your bitcoin also be tricky hardware wallets they remain the most effective in the safest way for the average user to safely store their crypto if you do not yet have a hardware wallet then please consider getting one is the safest way for the average user tips successfully store their crypto whether you choose a paper or a software or a hardware wallet always maintain the best practices right down in keep at least two copies of your keys or your passphrase and always do this using pen and paper laminated if you can of course rent water damage as well and then take those copies and put them in different places very simple stuff here are very important make sure you put it somewhere completely just not obvious and something in which a thief would never consider taking like Jane Austen book or something like that never store your keys online either you have a high risk of losing your crypto if you do your crypto can be gone in an instant if you don’t properly secure it if you do need a hardware wallet then ledger currently has an. Awesome sale going on we can actually get a family pack or a backup packs you can get yourself a whole big pile ledgers not me personally I always have multiple devices on hand collection Animax ledger nano S. and dental X. in the box this is just in case I lose water in case one of these devices get stolen and I can just take my passphrase set it up on the new device and I’m back in business a past Fraser had an incredibly secure and hard to find places so I feel quite comfortable about my back up for my security and of course either someone actually does steal your ledger wallet it just resets after three failed log in attempts so it’s very very secure the device is a very good place to keep your crypto there’s a link down below we can get yourself a ledger and also include a video tutorial for the ledger which will actually answer many of the common questions that people seem to have about using one of these devices please please please take your security seriously all of your years of stacking stats can be invalidated in a minute of crime so please take it seriously and finally the big story of today is that over the weekend a number of major decentralized finance exploits have happened to someone took advantage of the known exploit in the E. R. C. seven seven token standard to steal three hundred thousand dollars in Ethereum and wrapped a bit coin from a unique swap tokom pool there’s also been a critical vulnerability which has been found by the curve team in the synthetics S. U. S. D. contract now the vulnerability was found before anything bad happened all the funds are safe there has been no lost the vulnerability is currently being fixed actually the team has done really well here to act proactively to prevent any exploits of that vulnerability from happening this is why using H.. Rusted professional decentralized finance application like synthetics is so important in the first place because you have people working actively on the development of that product which you can trust but the big one of the weekend has to be this one lending protocols land F. dot and he was happy for twenty-five million dollars in crypto. The hacker drain basically all of the funds on the platform so this graph here you can see so eloquently illustrates how quickly the crypto disappeared from this platform and the hackers in a very savage follow up even sent a few thousand dollars worth of taxes tokens back to the team with a little note attached on the blockchain better future burn man that hurts yes split was again a known attack vector that took advantage of the known smart contract vulnerability now lend F. dot M. eat came under a lot of criticism actually hasn’t actually deployed and then apparently bastardized compound finances copyrighted code without consent and more critically it is apparent that the codes thieves not only lack the knowledge to develop their own smart contracts but they also lack the knowledge to properly maintain the smart contracts in to know how to audit for security vulnerabilities twenty five million Bucks in crypto gone. Just like that if there is a back door the hackers will find it there is no stopping and it’s their full-time job this is what they do but this for me just underlines that. It’s important to understand the risks remain in the decentralized finance space which is why for most people lending with someone like block fight for getting involved in lending is a much better option than landing on a lot of these decentralized markets however if you are going to be using a decentralized finance product then there are some things to keep in mind that you can use to keep yourself safe first off only use trusted and well established providers I’m talking the likes of kybernetwork and synthetics and compound finance their teams that have proven that they have what it takes to stay ahead of the curve to find vulnerabilities before the bad guys do into fix that maybe really really proactive about their code bases of course never risk more than you can afford to lose on the fight either we are still in the early experimental stages of this technology mistakes will happen money will be lost also use insurance on your defy plays if you can’t companies like nexus mutual actually offer you the chance to ensure your funds against smart contract failure but they do not insure all companies so be very wary of new players like land after dot M. E. that are entering the market many of these guys they’re gonna be fly by night types of operations just riding the defy hype wave. More money will be lost in the fi you can count on it that being said I remain incredibly optimistic about the future of decentralized finance early adopters of this technology they’re taking risks that the rest of us can sleep easy in the future but if you are not up for the risks of decentralized finance or you do not understand the risks thing keep your bitcoin or your theory I’m just locked up on your ledger or if you do want to get into the lending market use a service like block fi they’re highly regulated highly compliant a lot saved a lot of these defy platforms but long term this technology layer which we see being built on open public networks like Ethereum will be fundamental in challenging the existing financial order and then massively disrupting it so I remain very bullish on the future of the fight your question for today what are you doing to keep your cryptocurrency secure in are you using any defy applications and if so do you fully understand the risks that you are taking would love to know down below in the comments section what you are doing to keep your crypto safe thank you so much watching today’s video massively appreciate as always the time to take a few days over here and watch this did talk about crypto currencies on the internet seriously none of this is possible values thank you so much and enjoy today’s video hit that thumbs up button make sure to subscribe to the channel if you are new around here long live the blockchain. Add the peace out the next time.
source https://www.cryptosharks.net/major-crypto-defi-hack-are-you-safe/
0 notes